Supply Chain Threat Protection
Expand identity threat protection across the extended workforce, including the entire vendor ecosystem
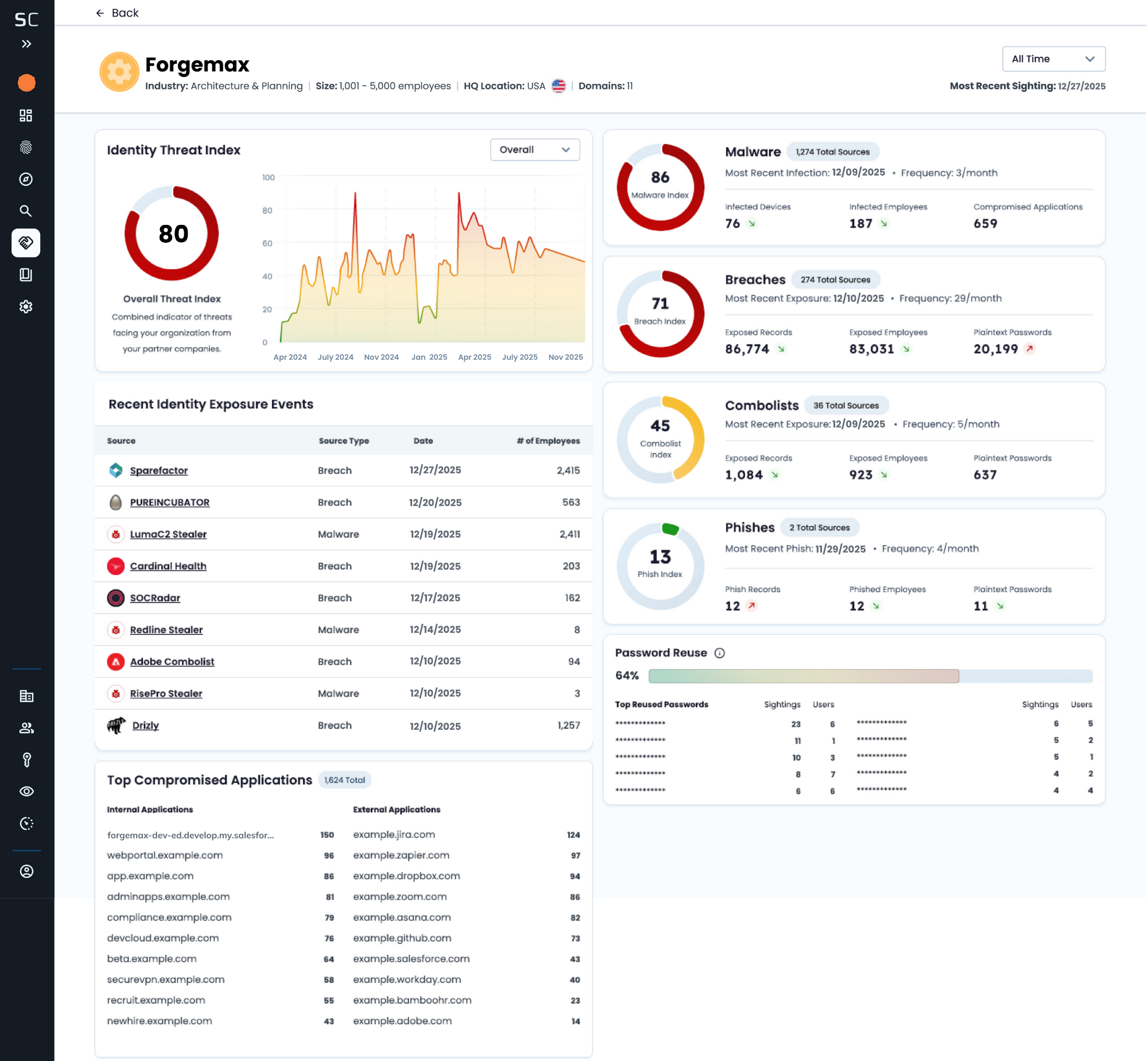
Monitor identity exposure across your supply-chain in one view, and drill in to analyze malware, phishing, breach, and credential exposure trends over time to reveal where identity threats are increasing, and why.
Overview
SpyCloud Supply Chain Threat Protection expands identity threat protection across your extended workforce – vendors, contractors, and partners. Instead of relying on surface indicators and static scores, it provides timely access to verified identity threats derived from recaptured breach, malware, phished, and combolist data, enabling teams to act on evidence.
The solution continuously analyzes vendor exposure through an Identity Threat Index that quantifies risk using recency, volume, credibility, and severity so you can prioritize response, engage vendors with proof, and reduce downstream risk.
Benefits at a glance
How it works
-
Add vendors and start monitoring
Add up to 1,000 vendors by domain and subdomain. SpyCloud recaptures and enriches data continuously, calculating a dynamic Identity Threat Index for each vendor. -
Detect exposures as they surface
See current index scores and the latest exposures by source type, with 12-month exposure trends. -
Understand what’s driving the risk
Review exposure events, numbers of affected employees, and consult the Source Catalog for data source details. -
Track vendor security over time
Measure improvements or degradation based on exposure frequency, recency, and severity. -
Investigate exposures that matter*
Initiate investigations on vendor assets (domain, machine ID, subdomain) directly from the SpyCloud console to assess potential business impact.
Requires SpyCloud Investigations license.
Key capabilities
Flexible Vendor List Management
Add, remove, or adjust monitored vendors on-demand to match changing business needs.
Threat Index Insights
Identity Threat Index across four data signals, broken down by source type to track posture changes.
Recent Exposure Visibility
Continuous view of the latest breaches, malware infections, phishing campaigns, and combolists affecting suppliers.
Detailed Source Information
Drill into data sources to identify trends and severity of threats per vendor.
Credential Hygiene Analysis
See prevalence of shared passwords across third-party employees to prioritize outreach.
Exposed Applications
Identify internal and third-party applications exposed on malware-infected supplier devices.
Updated about 1 month ago