Source Catalog
Overview of SpyCloud’s Source Catalog and how to understand the data SpyCloud publishes.
Getting Started with the Source Catalog
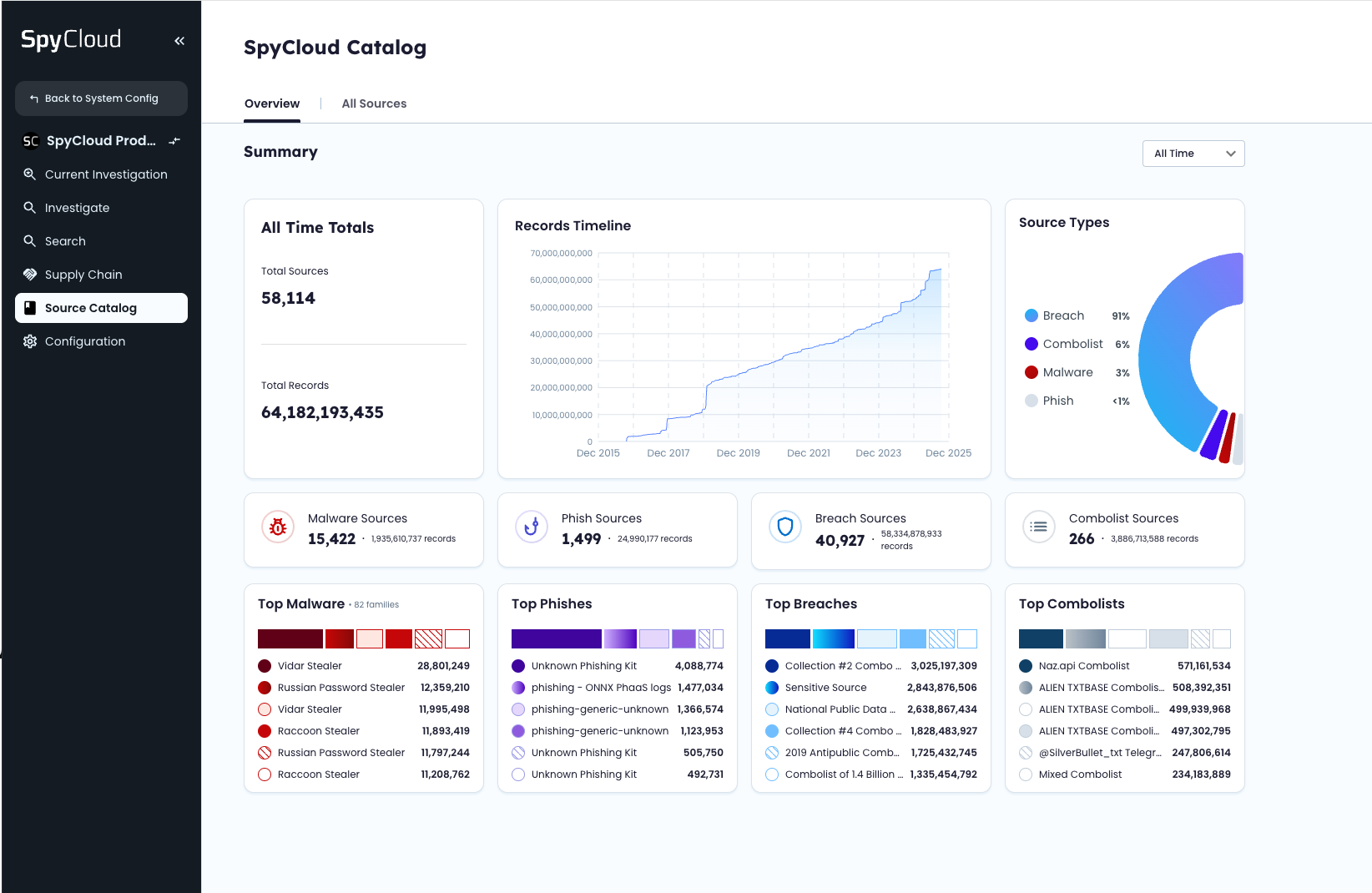
The SpyCloud Source Catalog is where our captured darknet data ecosystem comes to life – a daily view of the identity records SpyCloud continuously ingests, enriches, and publishes for customers. It’s available to all console users and provides a transparent look into the breadth, depth, and speed of SpyCloud’s recaptured data.
Why it matters?
The Source Catalog demonstrates SpyCloud’s unique visibility into criminal activity – not just third-party breaches, but infostealer malware infections, successful phishing attacks, and ULP (username login password) combo lists that reveal real-world identity threats.
Overview
The Source Catalog offers a high-level summary of all SpyCloud data sources, showing:
- Total number of published darknet records and total sources
- A timeline graph illustrating growth and publishing rate of data records
- A source-type breakdown (breach, malware, phishing, combo list)
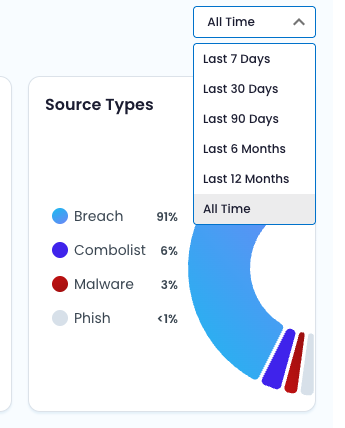
Adjusting the Timeframe
By default, the view shows All Time data. You can narrow the window to focus on more recent activity of publishing:
- Last 7 days
- Last 30 days
- Last 90 days
- Last 6 months
- Last 12 months
💡 Tip Filtering shorter timeframes shows the pace at which SpyCloud is publishing new data – a real indicator of data freshness and scale.
📘 Learn more: How SpyCloud Publishes and Updates Data
Understanding What You See
The source catalog provides aggregated insights into captured darknet data sources, not raw personal data or PII. You’ll see:
- Source IDs (useful for searching within each SpyCloud product)
- Record counts
- Types of exposed identity assets (e.g., passwords, emails, IP addresses)
These summaries reflect SpyCloud’s processed and enriched data — never direct PII.
📘 Learn more: SpyCloud Data Schema Reference
▶️ Source Catalog Overview
Next Steps
Updated 4 months ago