Elastic SIEM
Integration for SpyCloud Enterprise Protection
🧩 Enterprise Protection for Elastic SIEM
Leverage SpyCloud’s recaptured darknet data — including exposures from breaches, malware-infected devices, and successful phishing — inside Elastic Security to accelerate detection and remediation of identity-based threats (exposed credentials, infected sessions, risky users).
Integration page: https://spycloud.com/products/integrations/elastic-siem/
🚀 What you get (at a glance)
- Direct ingest of SpyCloud breach, malware, and phished exposure data into Elastic Security
- Comprehensive identity exposure visibility for improved detection & response across all three sources
- Elastic-native alerting & analysis — respond to SpyCloud records and push to your SOAR
- Out-of-the-box dashboards — confirm ingestion and visualize exposure trends from breach, malware, and phished datasets
Result: better signal on the who (identity) and the what (credentials, cookies, tokens) drawn from breach + malware + phished sources — with faster, automated response paths.
🛠️ How it works
1) Ingest — scheduled import of SpyCloud exposure records
SpyCloud’s Enterprise Protection for Elastic performs a scheduled ingest of exposure records derived from breaches, malware infections (infostealer logs), and phished credentials into Elastic. Once ingested, you can analyze records, create alerts, and route events for automation (e.g., to SOAR).
2) Analyze — search & correlate in Elastic
Use Elastic queries and visualizations to investigate exposure details, correlate identity artifacts with your telemetry, and identify high-risk users or systems — whether the evidence originated from a breach, malware, or a phish.
3) Alert — Elastic detections for new/high-risk exposures
Configure detections for fresh exposures, compromised credentials, infected sessions (malware-sourced cookies/tokens), or phished accounts. Alerts can drive timely ticketing and IR workflows.
4) Automate — handoff to SOAR playbooks
Push actionable SpyCloud events from Elastic to your SOAR for automated response (e.g., reset credentials, revoke sessions, force re-auth, disable accounts, notify users) — regardless of whether the originating evidence was from a breach, malware, or a phish.
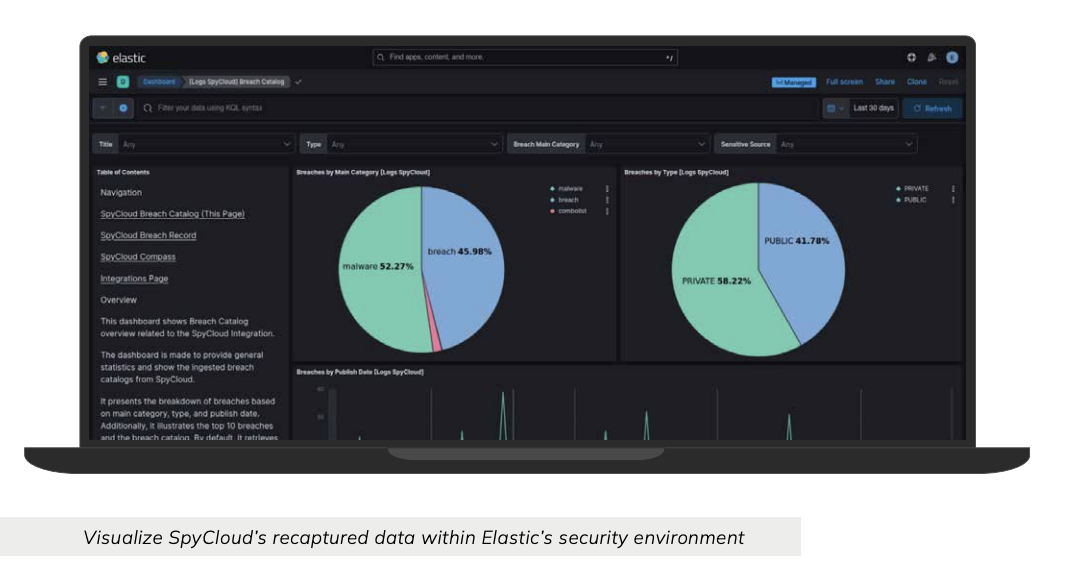
📊 Dashboards & visuals
Use the packaged dashboard(s) to confirm that data is flowing and to monitor exposure trends by source (breach, malware, phished) and by severity over time. Customize visualizations as needed.
🧭 Get started
- Visit the Elastic SIEM integration page for setup & resources: https://spycloud.com/products/integrations/elastic-siem/
- Connect ingest to bring SpyCloud Enterprise Protection exposure data (breach, malware, phished) into Elastic.
- Enable or create detections for new exposures and high-risk artifacts from any source.
- Wire SOAR handoffs for policy-driven remediation (resets, revocations, notifications).
- Validate flow using the dashboard, then iterate on queries/visuals.
Optional: Watch the Elastic integration demohttps://spycloud.com/products/integrations/elastic-siem/?wvideo=dnk5u1w6g6
✅ Outcome
- Higher-fidelity detection of identity-based threats from breach, malware, and phished exposures inside Elastic
- Faster, automated response via SOAR handoff (resets, revocations, re-auth, disable)
- Measurable reduction in exposure window for your workforce identities
Updated 29 days ago