Using the Source Catalog
How the Source Catalog supports detection, classification, and context across SpyCloud products
Using the Source Catalog
The Source Catalog isn’t just informational – it connects directly to how SpyCloud detects, classifies, and contextualizes identity exposures across your products.
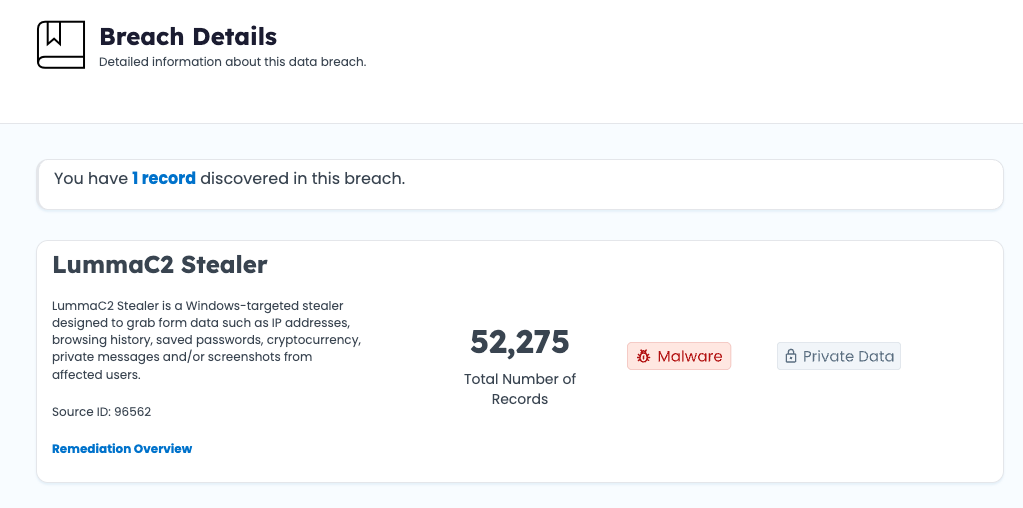
Viewing a Source
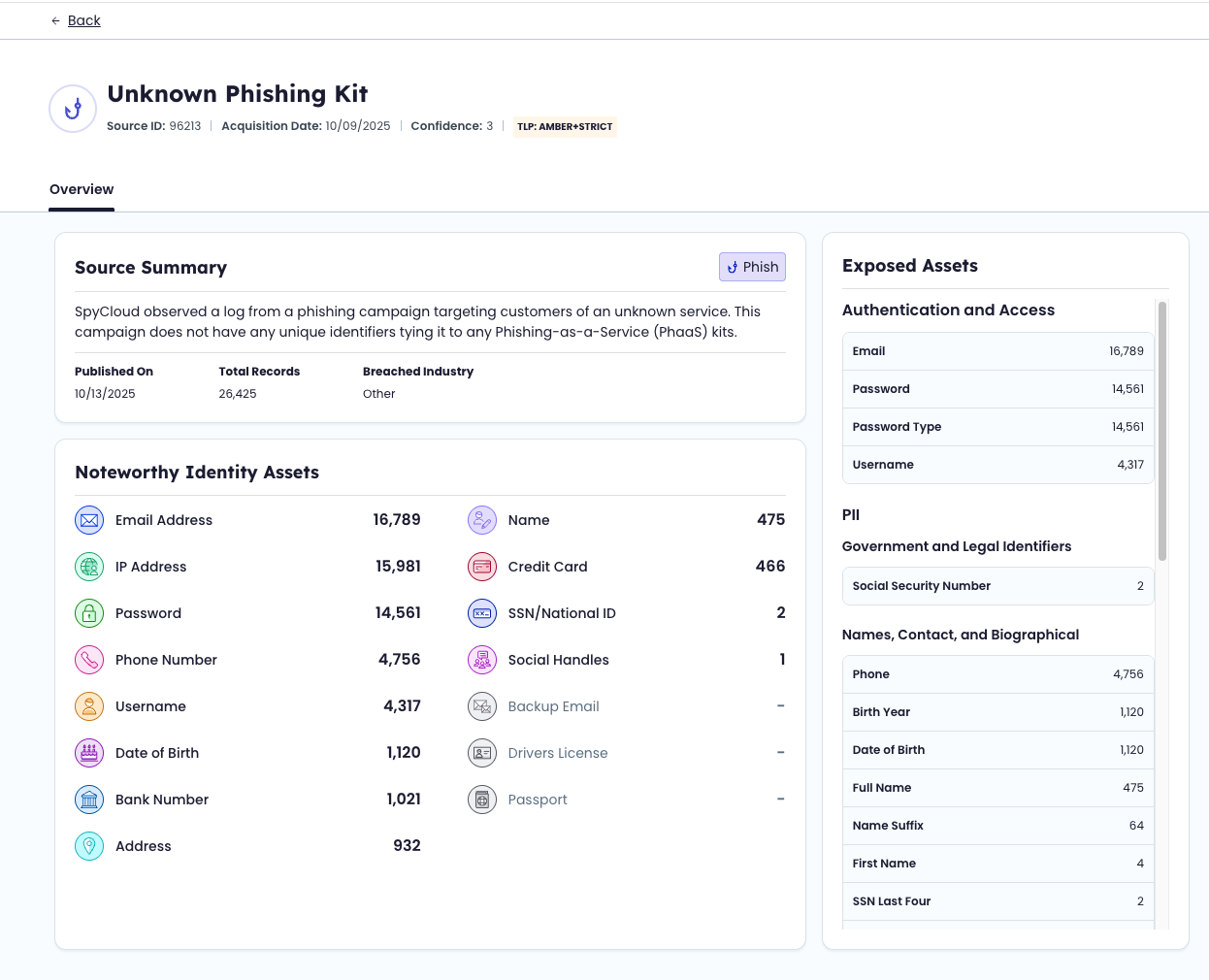
Selecting a source name opens its details page, showing:
- Source ID and publish date
- Record and device counts
- Exposure type(breach, malware, phishing, combo list)
- Summary of identity assets included
Interpreting Identity Assets
Each source summarizes the **categories of identity assets **contained within. Typical asset types:
- Emails, usernames, passwords
- IP addresses, device identifiers
- Financial and payment data
- Personal identifiers (e.g., DOBs, addresses)
💡 Tip The broader the asset coverage, the greater the chance criminals can recreate their own attempt of a holistic identity to target identity attacks – key for understanding potential threats
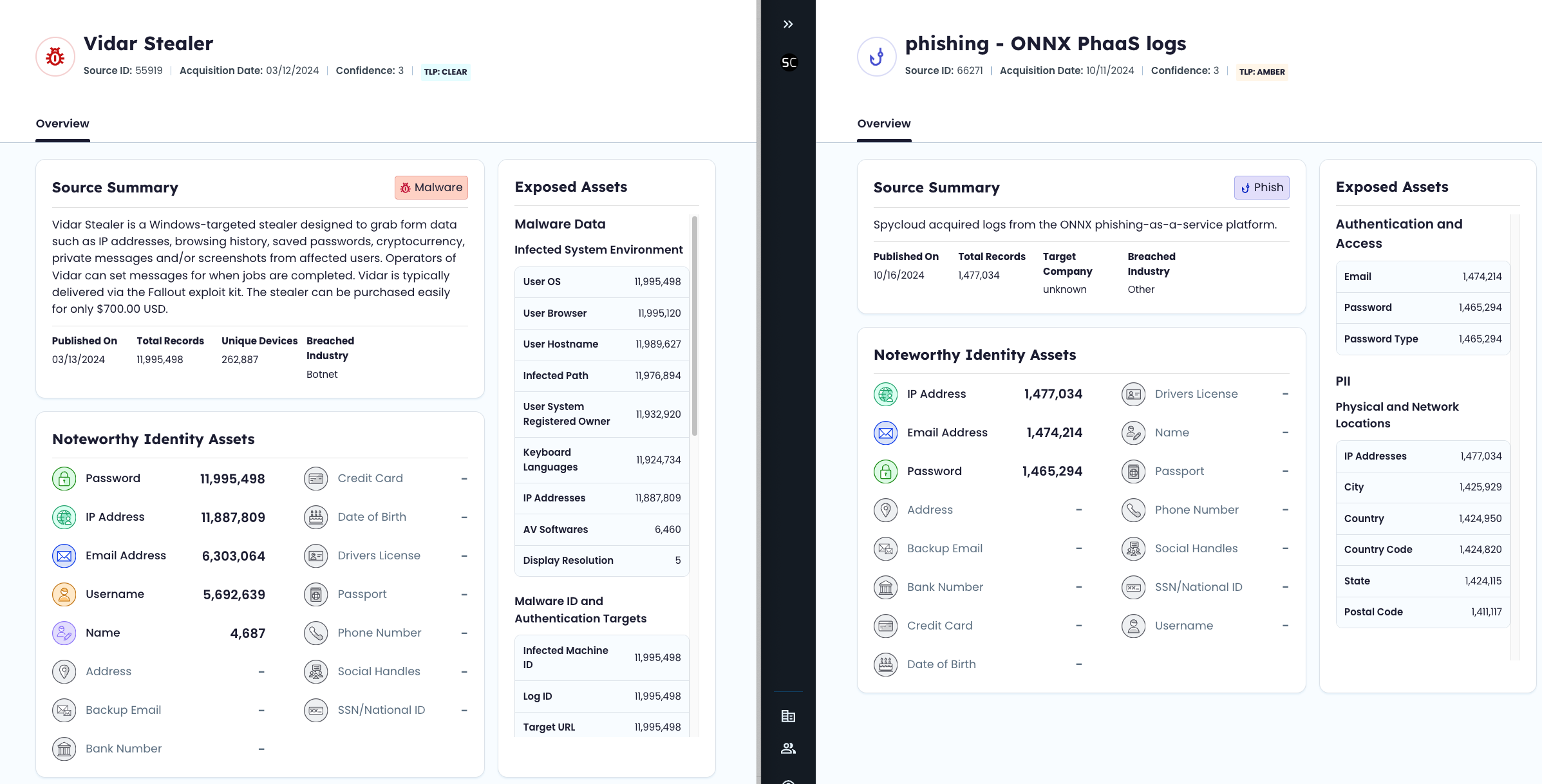
Examples of Source Analysis
Malware Source Example A stealer family may include infected device metadata, OS versions, and hundreds of application credentials.
Phishing Source Example A phishing kit might expose names, emails, phone numbers, and payment information from active campaigns.
Using Source IDs Across Products
Source IDs connect the dots between SpyCloud modules:
- Investigations: Discover where data originated and how it spreads.
- Employee ATO Prevention: Validate whether employee credentials came from a malware or phishing source. And map compromised records to their source to prioritize remediation.
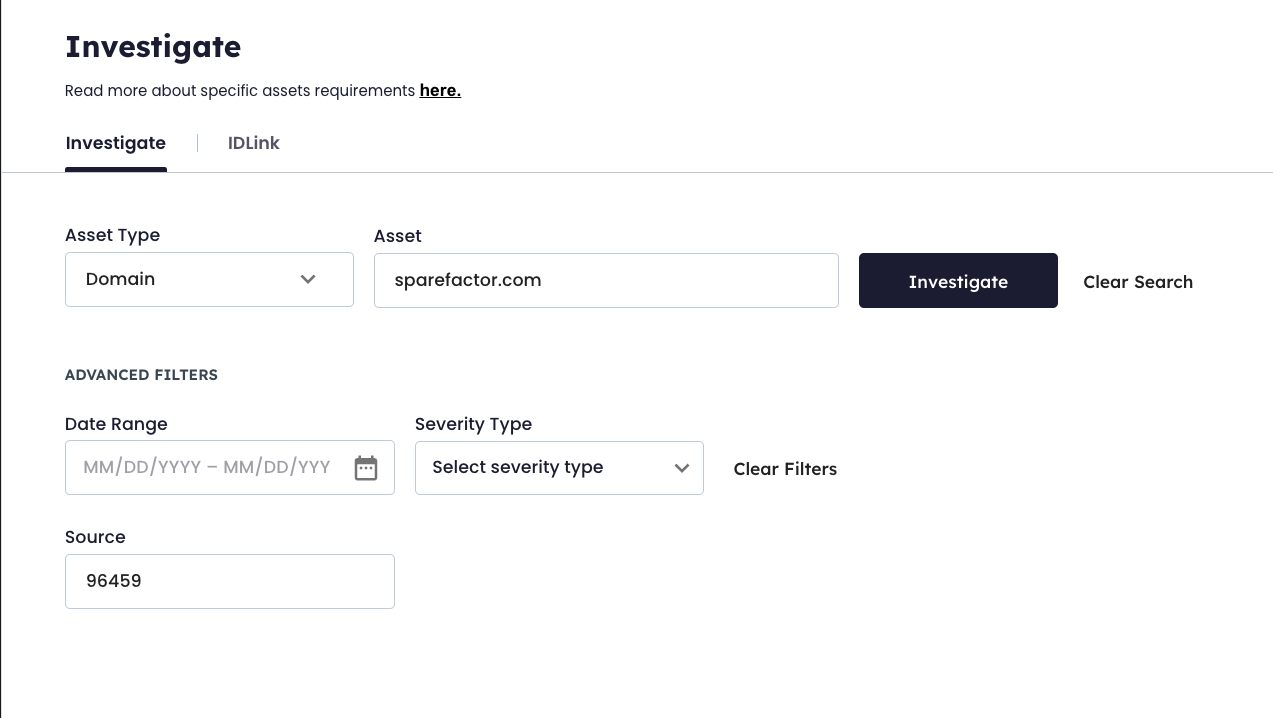
How to use Source ID within SpyCloud Investigations
When starting a new Investigation, you can paste Source ID in the field to focus your search to only recaptured data from this narrowed set. You could investigate a Domain, like “sparefactor.com” to explore records relevant to your domain that were included in the specific Source.
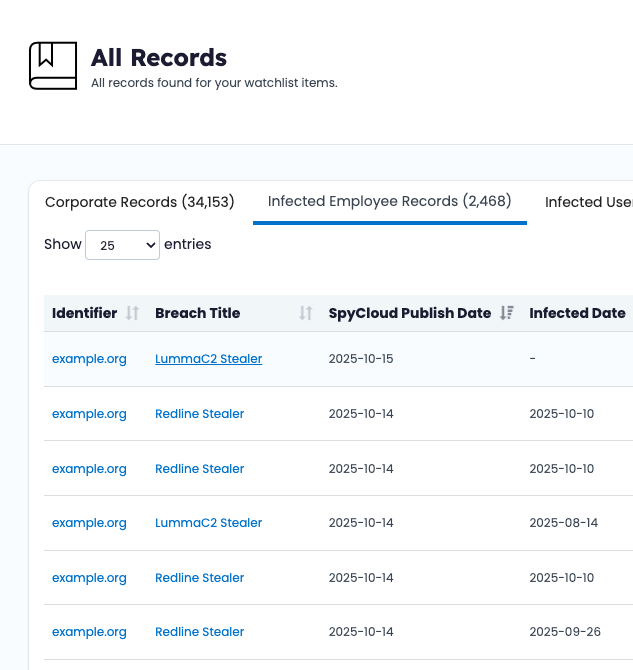
How to use Source ID within SpyCloud Enterprise Protection
When exploring a recently malware infected employee, the line item in the table references the name of the source. Clicking this “Detail” loads a view into the source itself to learn more, or copy the Source ID for future investigations.
Updated 4 months ago