Validating Identities in Cryptocurrency Exchange
USING SPYCLOUD INVESTIGATIONS MODULE
Example of a Good Application: Establishing a Real Identity
Subject Email: [email protected]
This example demonstrates a legitimate account registration submitted to a cryptocurrency exchange that passes identity verification using **SpyCloud Investigations Module **Pro License (with IDLink and AI Insights). The subject’s identity exhibits clear continuity across multiple digital touchpoints, historical data, and corroborating evidence. This serves as a benchmark for validating identities as part of Know Your Customer (KYC) processes and detecting synthetic identities.
IDLink Analysis Summary
| Attribute | SpyCloud Finding |
|---|---|
| Primary Email | [email protected] — confirmed in multiple historical breaches |
| Employment History | Previous corporate email(s) at @ebxtech.com recovered from historical datasets |
| LinkedIn Presence | Recovered LinkedIn profile (breached metadata) consistent with other data points |
| Phone Number | Validated Canadian number found in credential recovery flows and breach data |
| Geolocation | Consistent Canada-based IPs (Toronto, Montreal, Vancouver) in logs since 2017 |
| Breach Timeline | Records associated with this identity date back at least to 2017 |
Why This is a Good Identity
- Temporal Depth: Breach data and activity logs show a long-standing digital presence of over eight years
- Data Consistency: Email, phone, social, and professional metadata all align
- Low Risk Indicators: No evidence of inconsistent geolocation, fraudulent patterns, or obfuscation
- Rich Identity Graph: Emails, aliases, accounts, and online profiles are interconnected over time
This profile serves as a baseline for what a real, traceable identity should look like during KYC or account onboarding workflows. It contrasts sharply with synthetic or manipulated identities that lack this level of historical cohesion.
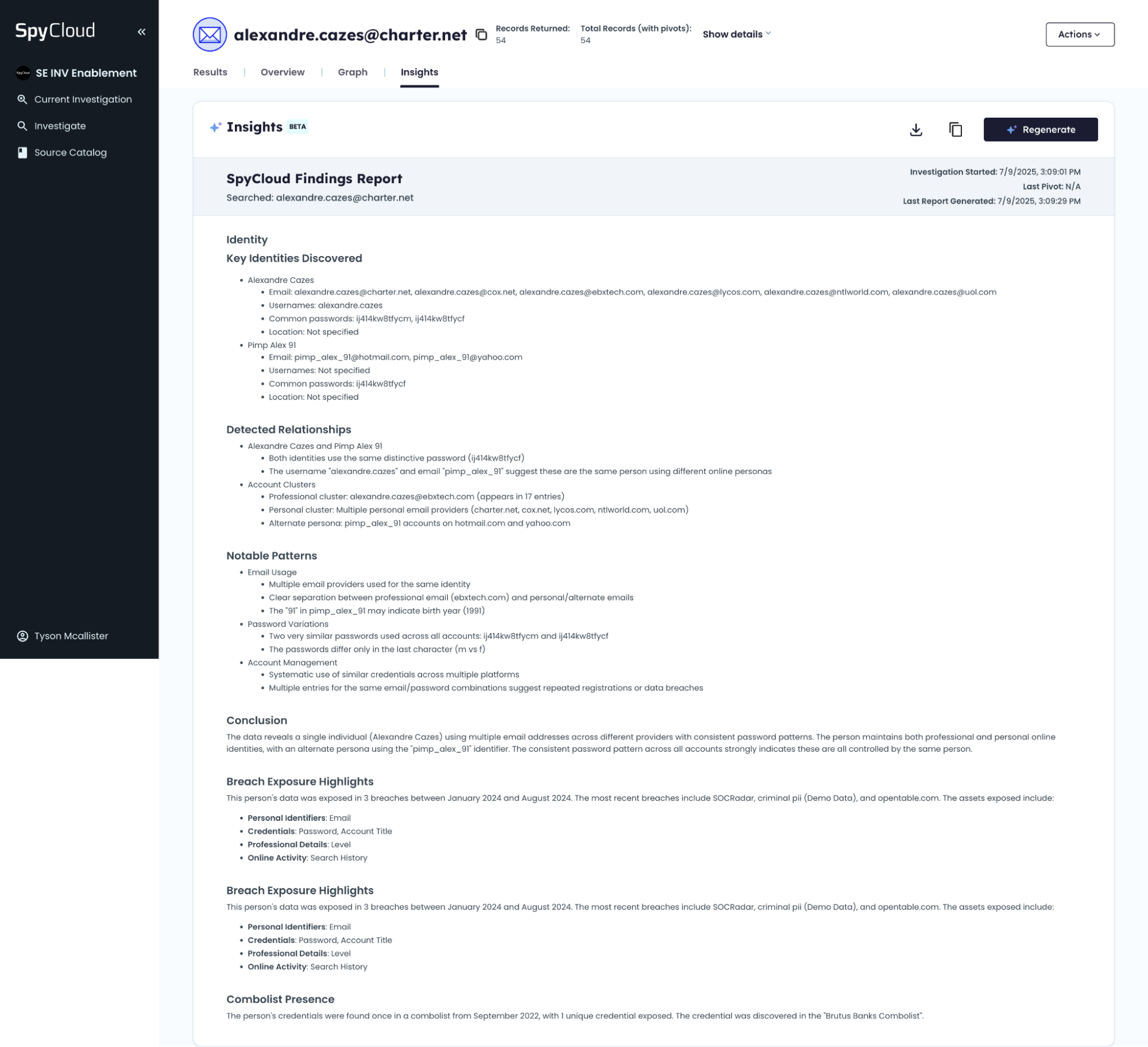
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
Example of a Suspicious Application: Potential Synthetic Identity
Subject Email: [email protected]
This identity was submitted during the account creation process at a digital asset exchange. When processed through SpyCloud’s IDLink with AI Insights, several inconsistencies and risk indicators were identified — typical of synthetic identity behavior. This highlights a failure scenario in KYC validation workflows.
IDLink Analysis Summary
| Attribute | SpyCloud Finding |
|---|---|
| Primary Email | [email protected] — no long-term historical activity found |
| Employment History | No prior corporate emails recovered; no verified work metadata |
| LinkedIn Presence | No linked or breached LinkedIn accounts associated with this email |
| Phone Number | Not found in breach data or recovery flows; not validated |
| Geolocation | IP data linked to regions inconsistent with claimed residence |
| Breach Timeline | No breach records tied to this identity prior to 2023 |
Red Flags Identified
- Lack of History: No breach records prior to 2023 — possibly newly created identity
- Missing Digital Footprint: No corroborating social media, employment, or credential data
- No Phone Confirmation: Phone number unlinked to breach or recovery data
- Geolocation Inconsistency: IPs don’t match claimed location — possible obfuscation
- No Cross-Linkage: IDLink fails to establish a rich identity graph or network of linked selectors
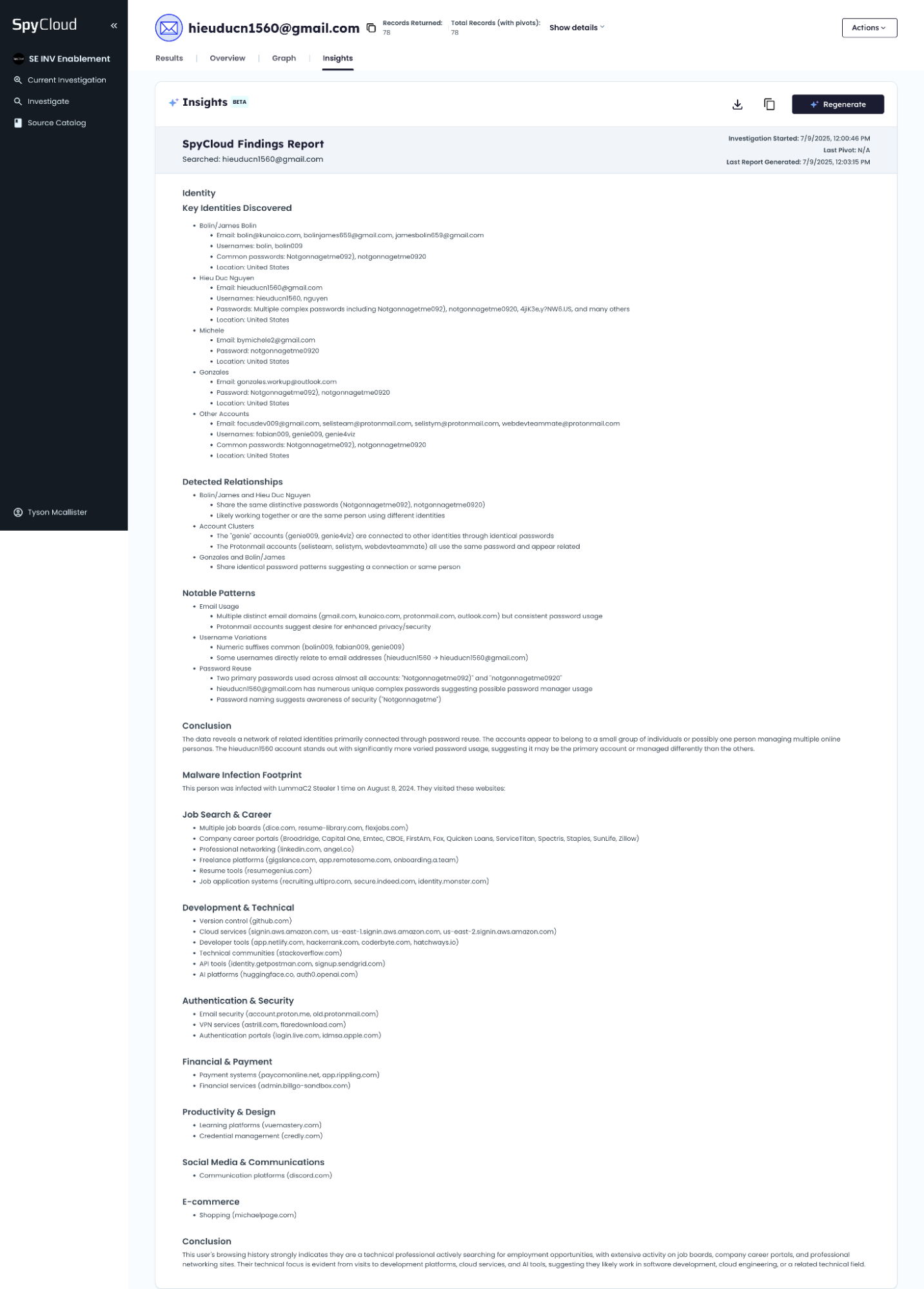
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
Assessment
This case demonstrates several typical red flags for synthetic identities or fraudulent applications:
- Minimal digital history
- No corroborated personal or professional data
- Region-hopping or obfuscated geolocation behavior
Such applications are high-risk for fraud or automated identity generation and warrant deeper investigation, secondary verification, or outright rejection depending on your organization’s KYC requirements and fraud prevention protocols.
The examples featured in this guide are drawn from real-world breach data to showcase how SpyCloud AI Insights enhances identity investigations. They are intended to demonstrate product capabilities and reflect common patterns our platform uncovers in compromised identity ecosystems.
While based on actual breach intelligence, these case studies are provided for illustrative purposes only. SpyCloud does not make determinations about individual intent or behavior, and the inclusion of specific data points does not imply malicious activity.
Updated 6 months ago