Detecting Evidence of DPRK Remote IT Workers
USING SPYCLOUD INVESTIGATIONS MODULE
SpyCloud Investigation: Detecting DPRK Remote IT Worker Employment Fraud
North Korean state-sponsored actors have increasingly infiltrated Western organizations through sophisticated employment fraud schemes. These remote IT workers use false identities and stolen credentials to secure legitimate positions, then exploit their access for espionage, intellectual property theft, and revenue generation to circumvent international sanctions.
SpyCloud has observed many of these DPRK fraudulent IT workers inadvertently infect their own workstations with commodity infostealer malware. These self-infections provide unprecedented visibility into their operational tactics, tools, and procedures (TTPs), revealing substantial information about their daily digital activities and organizational targets.
This investigation demonstrates how to identify DPRK remote workers using SpyCloud Investigations with AI Insights.
Step 1: Initial Domain Pivot - VPN Infrastructure Discovery
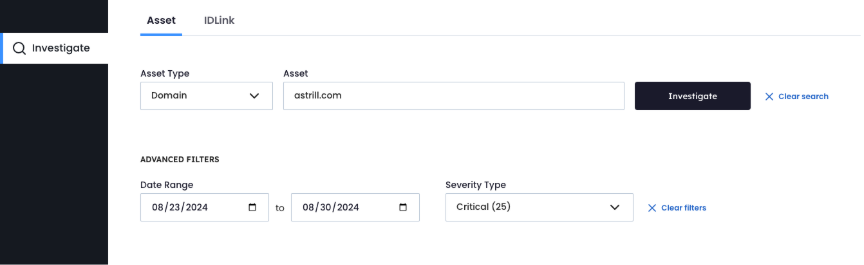
The investigation begins by targeting known VPN services heavily used by DPRK workers to obfuscate their true geographical locations.
Key actions:
- Navigate to Asset Type section
- Perform domain search using:
astrill.com - Select Severity Type 25 to focus on malware infections
- Prioritize results with highest record counts
Why Astrill VPN:
- DPRK workers primarily operate from Russia and China. Astrill provides reliable access to circumvent regional restrictions, and historical intelligence confirms heavy usage in this campaign
What to Look For:
- High-volume IP addresses with multiple associated records
- Consistent geographical patterns (Russia/China-based IPs)
- Device fingerprints showing enterprise software access
INVESTIGATE AT THE DOMAIN LEVEL
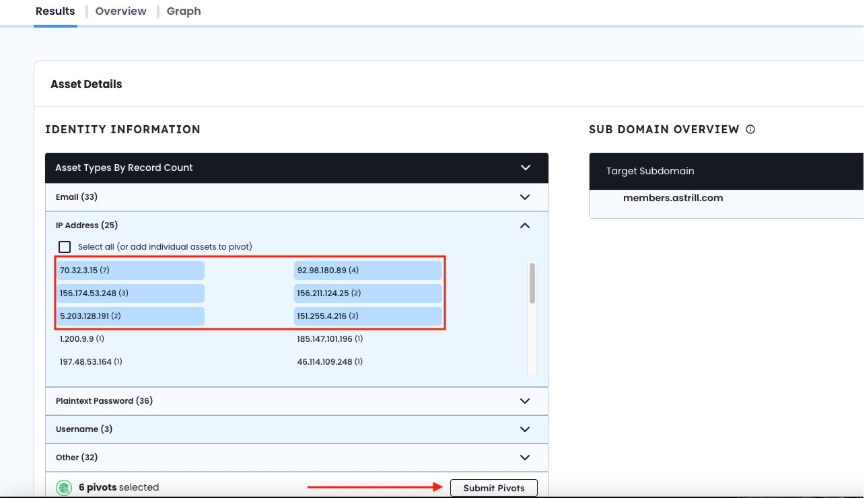
Step 2: Identify High-Activity IP Address
From initial results, focus on exposed IP Addresses with the highest record counts to identify more signs that could signify any common DPRK worker activity.
Key actions:
- Select IP addresses with highest record counts in the “Baseball Card” table
- Click "Submit Pivots" to ingest additional darknet data, beyond the initial Astrill data that you started with.
- See the "Total Records" count increase (typically 2000+ records)
- Document geographical consistency and access patterns
Indicators to Monitor:
- Single devices with extensive job platform activity
- Multiple identity management across shared systems
- Enterprise collaboration tool usage patterns
- Consistent password reuse across identities
SELECT MULTIPLE IP ADDRESSES TO PERFORM ADDITIONAL PIVOTS
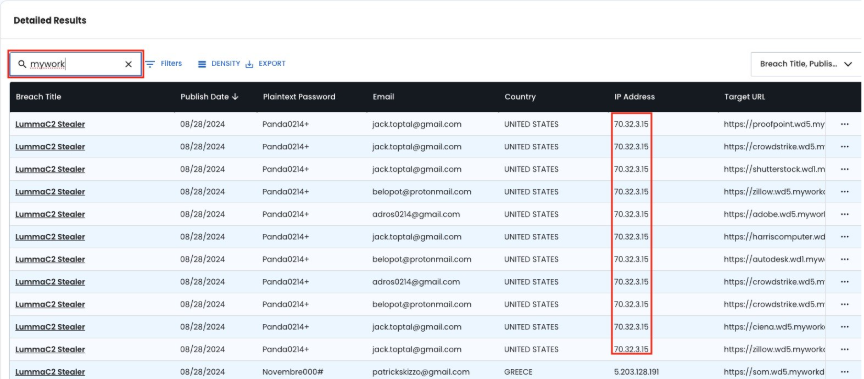
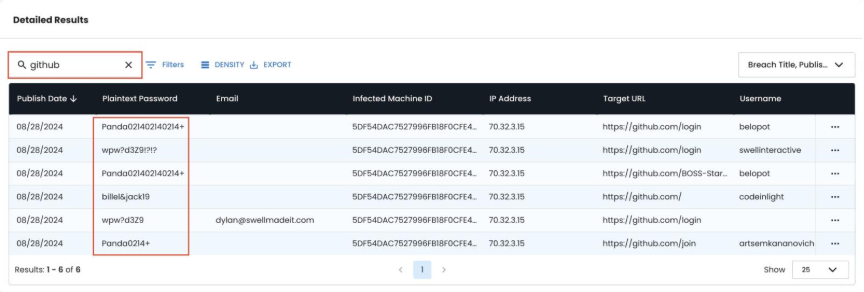
Step 3: Job Platform Activity Analysis
Search for employment-related keywords to identify systems engaged in fraudulent hiring activities. DPRK IT workers use job application platforms like Workday, Taleo, BrassRing and others to apply for jobs and we want to identify systems that have a lot of Workday or other job platform connections.
Key search terms: mywork, workday, taleo, brassring
- Corporate email domains and HR platforms
- Remote work collaboration tools
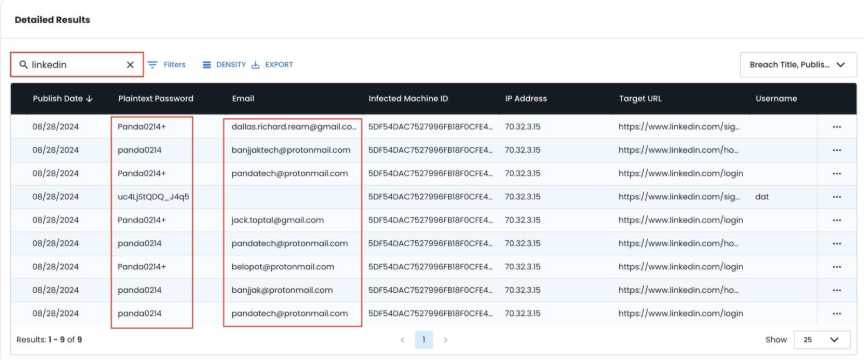
Critical Finding Pattern: Multiple email identities using identical passwords (e.g., Panda0214+) indicates:
- Single actor managing multiple false identities
- Systematic approach to employment fraud
- Operational security lapses revealing true scope
- WHY? Different people using a shared system would typically have different passwords.
What to Look For:
- Multiple Job Platforms
linkedin.com,workday.com,greenhouse.io,lever.co,smartrecruiters.com,icims.com
- Identity Management Tools
- Password managers with multiple profiles; Identity verification document tools; VPN switching between applications
- Collaboration Platform Access
slack.com,teams.microsoft.com,github.com,gitlab.com,teamviewer.com,anydesk.com
FILTER BY IP AND DOMAINS
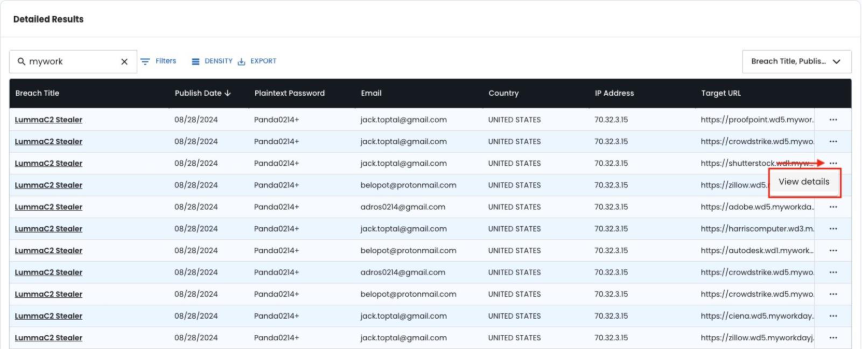
Step 4: Device Isolation and Deep Analysis
Once suspicious activity is identified, isolate the specific device for comprehensive analysis and followup investigations. This new investigation will now return all of the records captured by the info stealer on this specific device.
Key actions:
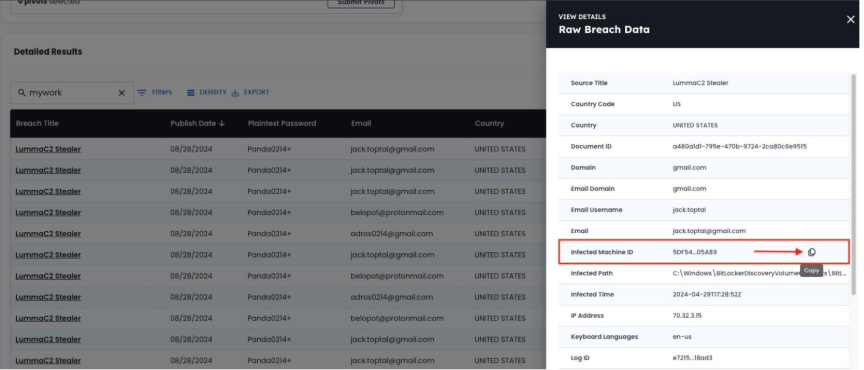
- Extract Infected Machine ID from detailed record view
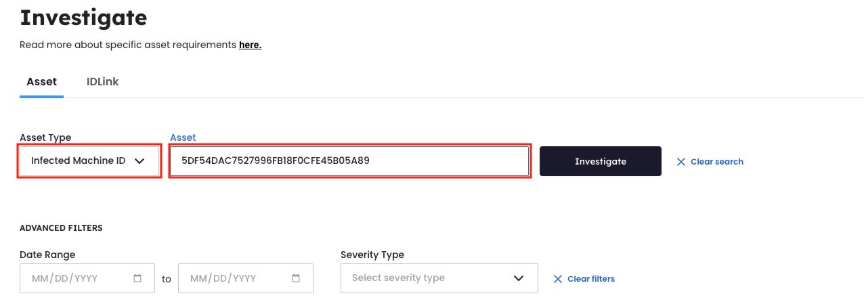
- Run new search using "Infected Machine ID" asset type
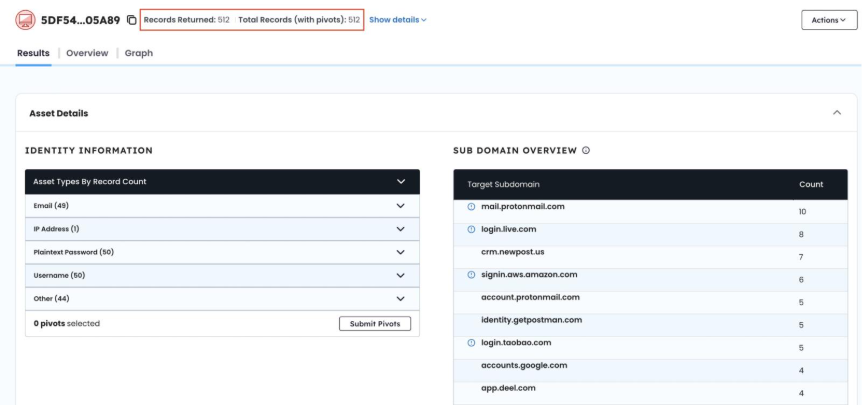
- Analyze complete device footprint (typically 500+ records)
Device Analysis Framework:
- Operating System: Windows 10 Pro (corporate standard)
- Geolocation: Russia/China IPs with VPN usage
- Software Profile: Enterprise development tools
- Access Patterns: Business hours activity in target timezone
Critical Indicators:
- Remote access tools (TeamViewer, AnyDesk, Chrome Remote Desktop)
- Multiple LinkedIn profiles (2+ accounts = high fraud indicator)
- AI/translation services (language barrier mitigation)
- Cryptocurrency platforms (payment obfuscation)
- Why? Things like LinkedIn, Slack, GitHub, TeamViewer, AnyDesk, AI platforms, language translation services are tools used in the campaign. Any additional job board connections can signal remote employment efforts.
CLICK TO VIEW DETAILS FOR RECAPTURED RECORDS
COPY INFECTED MACHINE ID FOR NEW INVESTIGATION
START NEW INVESTIGATION WITH ‘INFECTED MACHINE ID ‘ ASSET TYPE
EXPLORE EVERY RECORD SPYCLOUD FOUND FROM INFECTED DEVICE
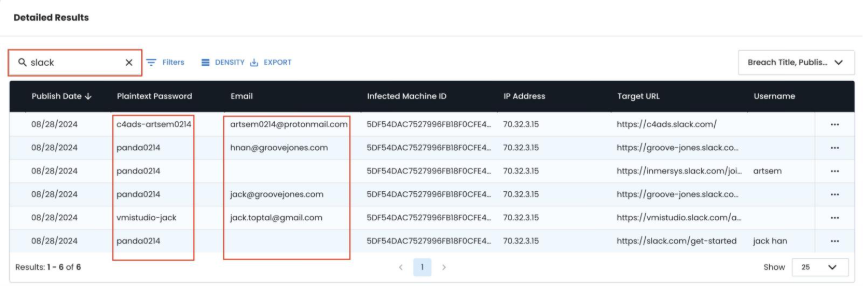
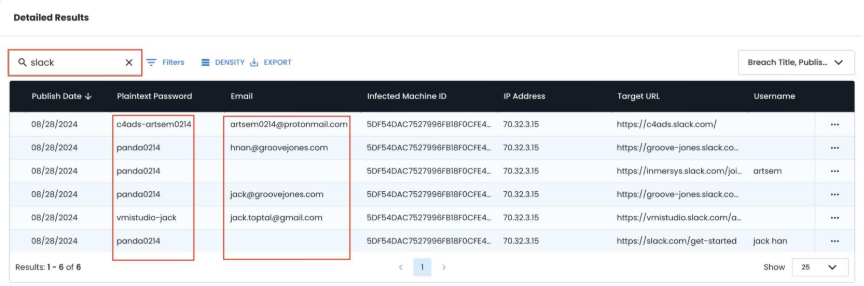
Step 5: Multi-Identity Pattern Recognition
Analyze credential patterns to map the full scope of false identity operations. Search through the records for activity related to other job platforms and collaborative tools that are known to be used in the campaign. Things like LinkedIn, Slack, GitHub, TeamViewer, AnyDesk, AI platforms, language translation services are tools used in the campaign. Any additional job board connections can signal remote employment efforts.
LinkedIn Account Analysis:
- Red Flag: More than 2 LinkedIn accounts per infected device
- Pattern: Consistent password schemes across profiles
- Validation: Cross-reference employment history consistency
MULTIPLE LINKEDIN PROFILES COULD BE A RED FLAG
GITHUB RECORDS COULD BE OTHER INDICATORS
SLACK RECORDS COULD BE OTHER INDICATORS
Password Reuse Patterns:
- Same base password + variations across identities
- Seasonal/date-based modifications (e.g.,
Panda0214+,Panda0224+) - Consistent complexity meeting corporate requirements
TEAMVIEWER IS COMMONLY USED BY DPRK ACTORS
Step 6: AI Insights – Generate a Findings Report
Turn your investigation signals into a polished, shareable report that captures key findings and supporting evidence of compromise to help your next steps.
What it does (at a glance):
- Synthesizes exposure data you surfaced in Steps 1–5 (VPN use, multi-identity behavior, job platform activity, remote tools, password reuse, geo anomalies).
- Correlates assets (emails, usernames, domains, machine IDs, IPs) and highlights known identities.
Key actions:
- Click Generate in the Insights tab
- AI Insights collects:
- All records from your searches
- All records added through pivots
👇FINDINGS REPORT
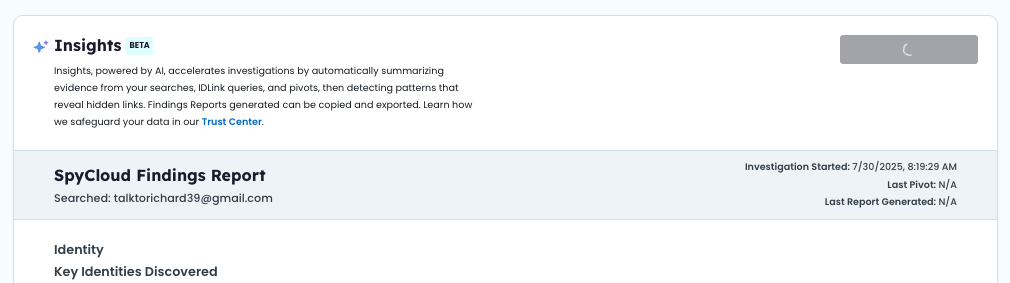
📋 Report Details
🧑 Identity
Key Identities Discovered
Enumerates each distinct individual, listing:
- Primary and secondary emails
- Observed aliases and usernames
- Common or reused passwords
- Inferred location (if present)
Detected Relationships
Narrative bullets describing:
- Credential sharing
- Overlapping infrastructure
- Other linkages that indicate aliases or cooperation
Notable Patterns
Highlights of:
- Naming conventions
- Credential-reuse themes
- Geography clutering, etc.
Conclusion
Concise assessment tying the identities together and noting investigative implications.
🐛 Malware Infection Footprint
Infection Timeline
- Malware family names (e.g., Redline, Mars Stealer)
- Infection count and publish date range
Visited Websites
- Categorized by context:
- Job Search
- AI Tools
- E-commerce
- Authentication & Security
- Developmental & Technical
- Productivity & Design
- Authentication & Security
Conclusion
Analyst summary of behavioural themes or intent suggested by browsing activity.
🔓 Breach Exposure Highlights
📦 Combolist Presence
📎 Appendix
⚠️ ASSESSMENT This investigation pattern indicates sophisticated state-sponsored employment fraud with the following characteristics:
- Professional operational security with systematic identity management
- Enterprise target focus through legitimate employment channels
- Technology sector specialization via development role infiltration
- Revenue generation model combining espionage with direct payment
This method highlights potential indicators, not definitive proof of threat actors.
Common Questions
When should I use the Investigations graph view?
Use the graph view when you need to visualize relationships between multiple identities, devices, or organizations. It’s especially useful for mapping the full scope of infiltration and uncovering connections that aren’t obvious in list-based results.
What if initial VPN searches don't yield results?
If early searches come up empty, pivot to alternative asset types:
- Corporate email domains
- Remote access tools
- Development platform domains
Remember: DPRK workers adapt their infrastructure regularly, so stay flexible with search parameters.
How do I distinguish between legitimate remote workers and DPRK actors?
Look for combined indicators such as:
- Multiple identity management across unrelated accounts
- Geographical inconsistencies in login patterns
- Password reuse patterns across different assets
- Access to sensitive development resources paired with VPN activity
Taken together, these patterns often signal coordinated, non-legitimate activity.
The examples featured in this guide are drawn from real-world exposure data to showcase how SpyCloud Investigations enhances your existing insider threat detection capabilities. The examples are intended to demonstrate product capabilities and reflect common patterns our product uncovers in compromised ecosystems.
While based on actual recaptured darknet data, these examples are provided for illustrative purposes only. SpyCloud does not make determinations about individual intent or behavior, and the inclusion of specific data points does not imply malicious activity.
Updated 4 months ago