Exploring and Filtering Sources
How to browse, filter, and search Source Catalog data.
The Source Catalog is interactive – built to help you explore where SpyCloud’s identity data originates and how it evolves over time. Filters and search options make it easy to find the most relevant sources for better understanding any exposures or for accelerating your investigations.
Browsing the Data
Switch between:
- Timeline view – visualize ingestion and publishing trends, with summaries of the most recent ingestions per data type
- Table view – explore detailed information and metadata within each recaptured record
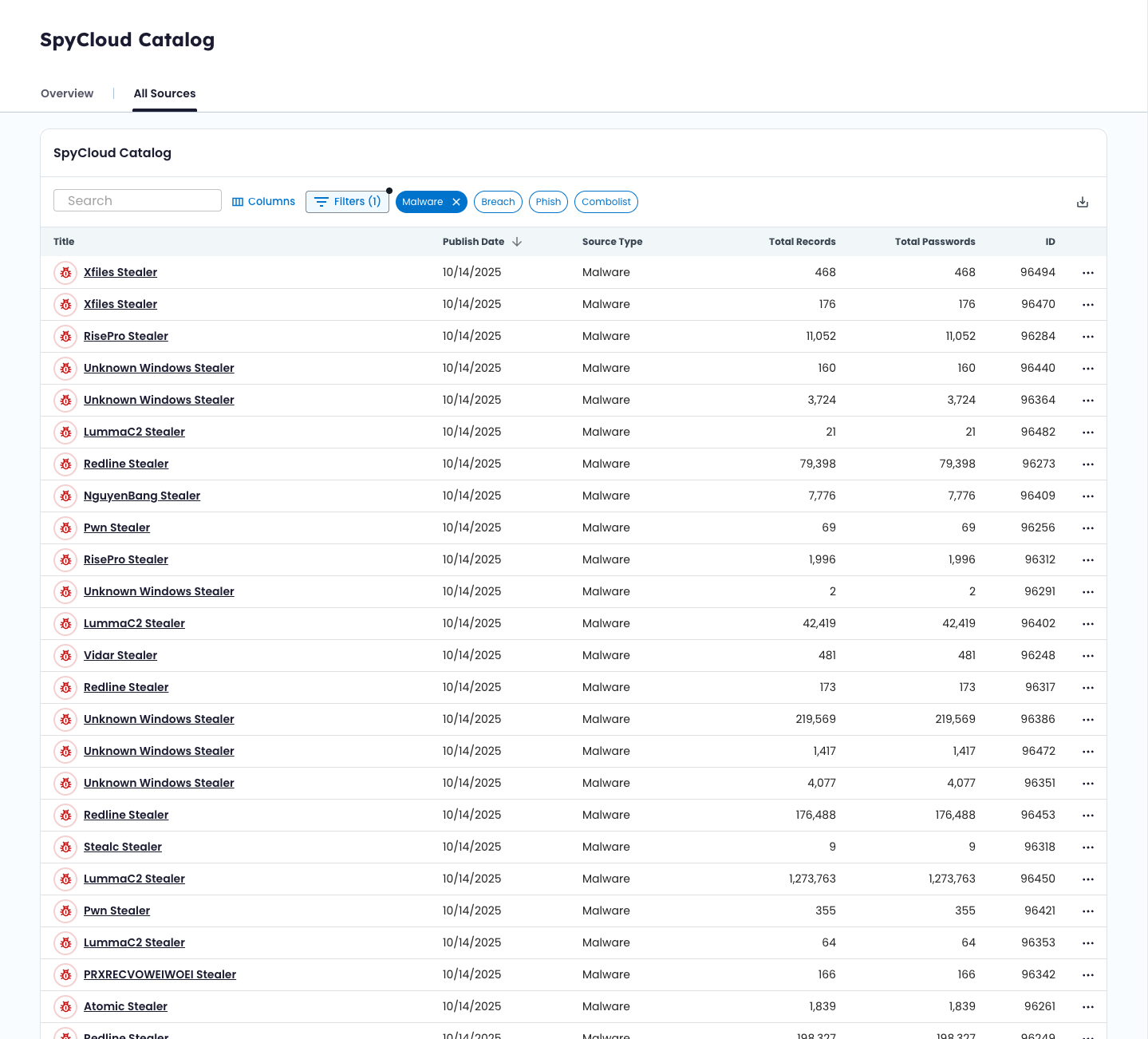
Each row represents a unique data source SpyCloud has published.
Filtering by Date and Type
Refine your view using filters:
- Timeframe: Choose from preselected ranges like last 7 days, last 90 days, all the way to All Time
- Source Type: Malware, Phishing, Breach, Combo List
- Keyword: Search by source name, malware family, phishing campaign, or other datapoints
💡 Did you know? New malware and phishing records appear here shortly after ingestion – one of the fastest ways to see identity exposures SpyCloud has captured.
Understanding the Table View
Columns include:
- Title / Short Title
- Source ID
- Published Date
- Source Type
- Total Records
- Total Passwords
- And more
You can sort, filter, or search any column and customize visible fields.
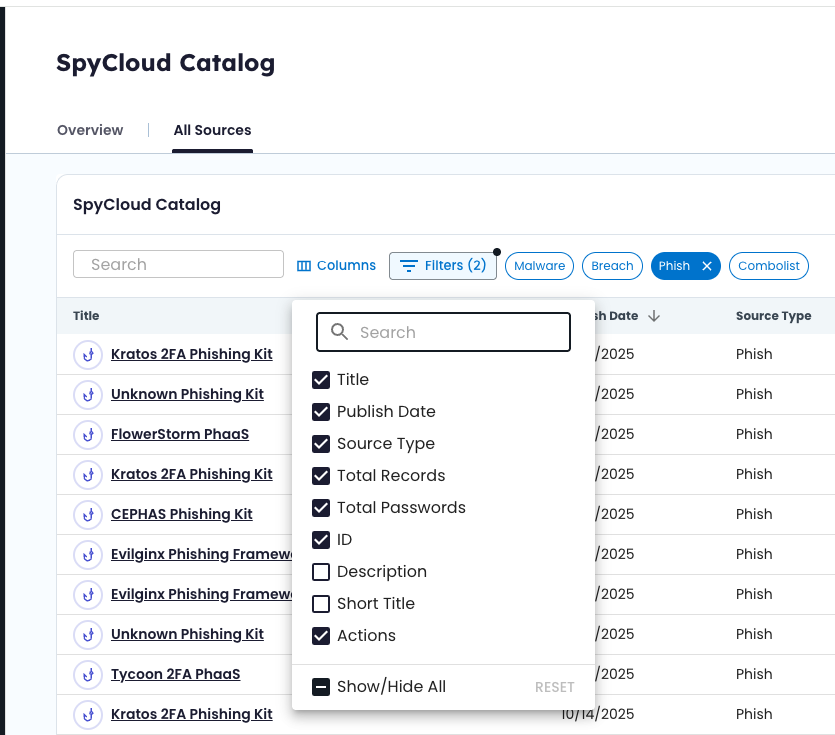
📘 Learn more: Catalog Field Descriptions
What Is a Source ID?
A Source ID is a unique identifier for every dataset SpyCloud processes. It acts as a digital fingerprint connecting SpyCloud’s data across modules.
Use Source IDs to:
- Cross-reference alerts in Investigations or Enterprise Protection offerings
- Trace exposures back to origin sources
Example Filter Combinations
| Goal | Example Filter Combinations |
|---|---|
| View recent malware infections | Type = Malware; Date = Last 30 days |
| Identify large phishing kits | Type = Phishing; Sort by Total Records (descending) |
| Check for noteworthy breaches | Type = Breach; Keyword = “NPD” |
Next Steps
After finding an interesting source, click its title to open Source Details and explore the exposed assets, metadata, and context.
Updated 4 months ago