Investigating a Hijacking Incident
USING SPYCLOUD INVESTIGATIONS MODULE
SpyCloud Investigation: Orange.es BGP Hijacking Incident
The Situation: Orange.es BGP Hijacking Incident
In January 2024, Orange España, a leading telecommunications provider in Spain, suffered a critical Border Gateway Protocol (BGP) hijacking attack that caused widespread internet connectivity disruptions affecting thousands of customers. The attacker, known by the alias Snow (also referenced as ms_snow_0w0), exploited weak password hygiene to gain unauthorized access to Orange’s RIPE NCC account. This allowed the actor to manipulate BGP routing and RPKI configurations, rerouting traffic and impacting network stability.
This incident highlights vulnerabilities in telecom infrastructure when credential security lapses occur — and underscores the need for strong identity management and proactive threat intelligence.
This investigation uses SpyCloud's threat intelligence to trace credential exposure and actor behavior across the following use cases:
Supply Chain Exposure Monitoring
Internal Threat & Compromised Employee Investigation
Compliance Exposure Investigations
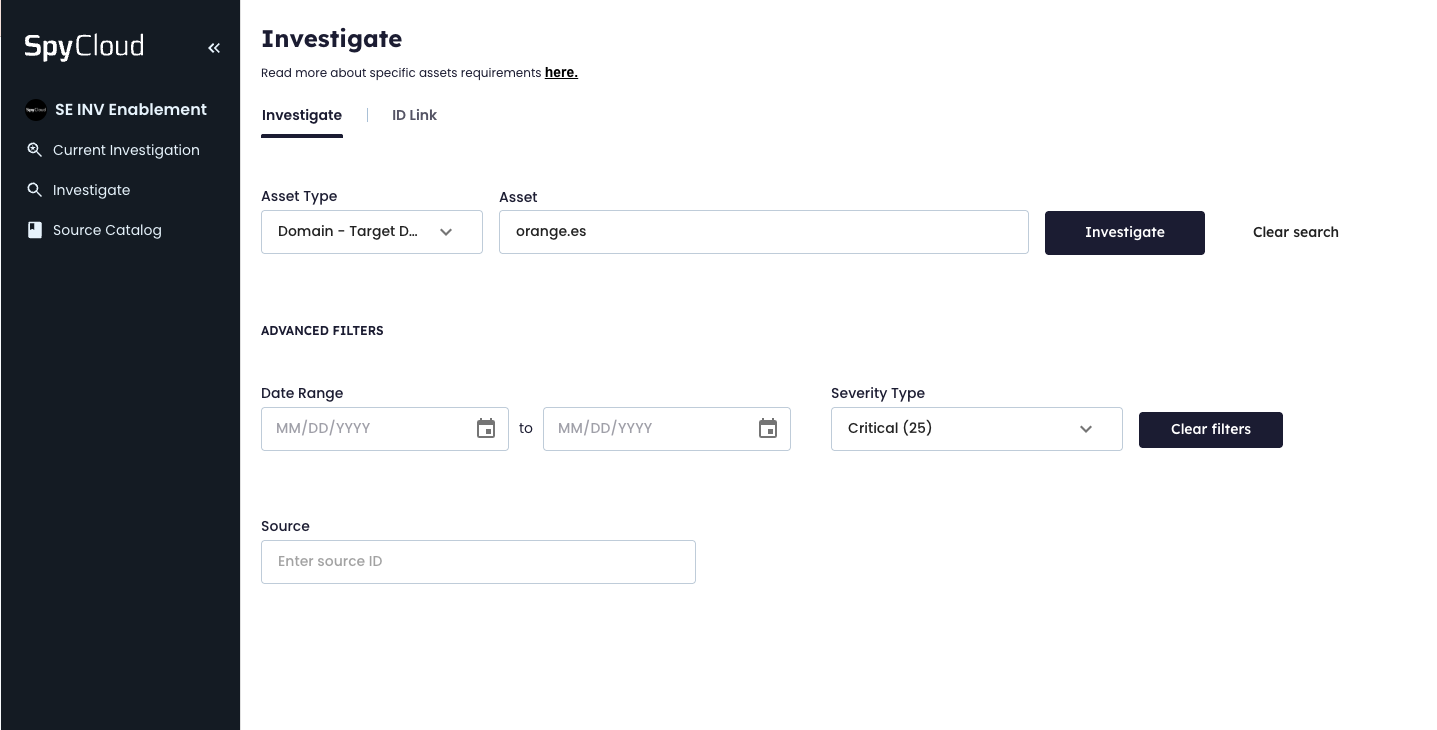
Step 1: Search for Orange.es Credentials by Email Domain
The investigation begins by querying SpyCloud’s breach data for credentials tied to the @orange.es domain — identifying potential employee or contractor account compromise.
Key actions:
- Filter for email addresses ending in
@orange.es - Prioritize credentials with Severity Level 25 (high confidence of compromise or malware infection)
- Analyze passwords and breach source
- Document high-severity credentials for response
👇 STARTING WITH DOMAIN SELECTOR
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
👇 SEE ASSET DETAILS
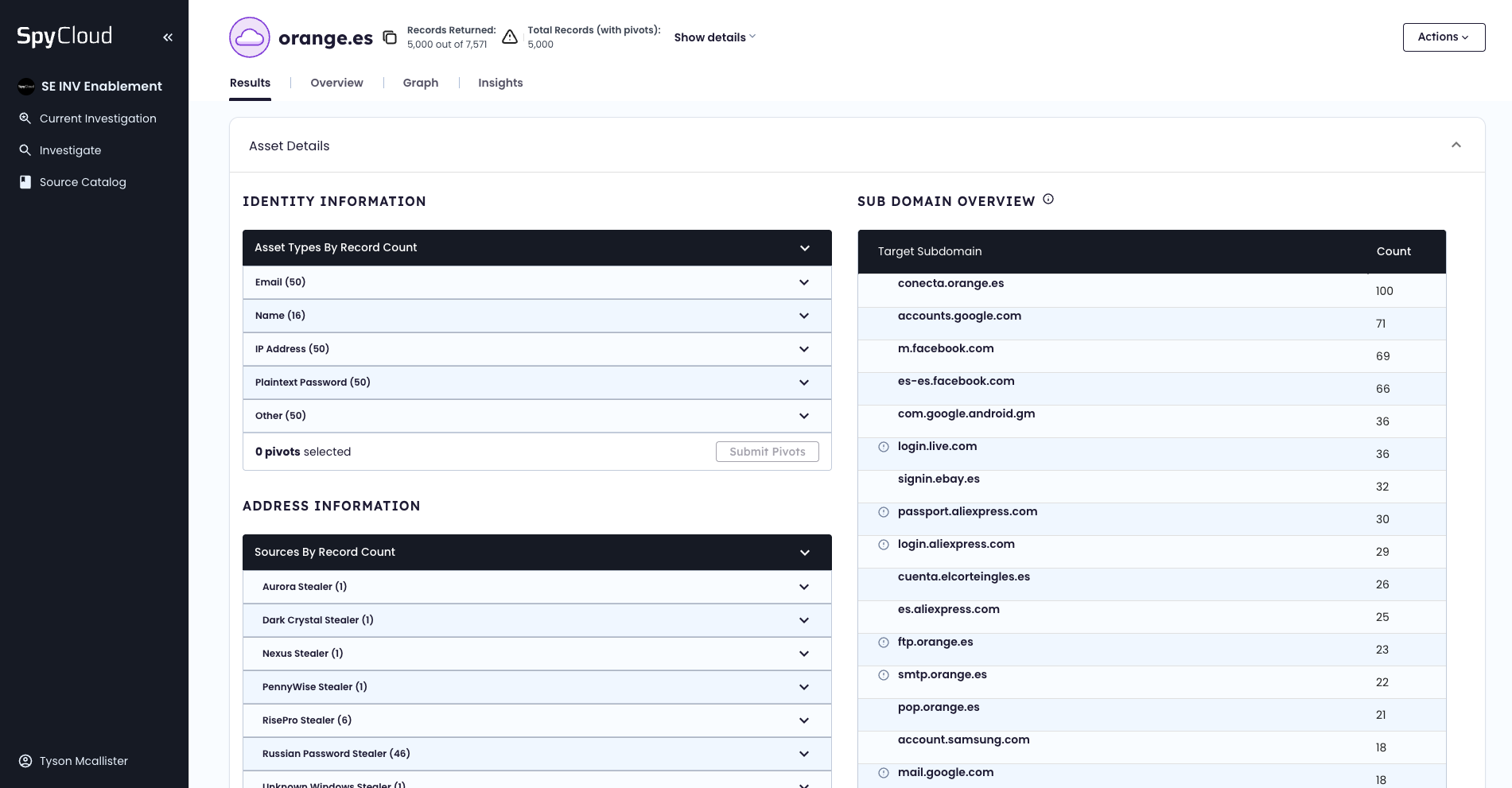
Step 2: Filter for Administrative Accounts
After identifying exposed credentials, the focus shifts to elevated access accounts — particularly those with "admin" in the email.
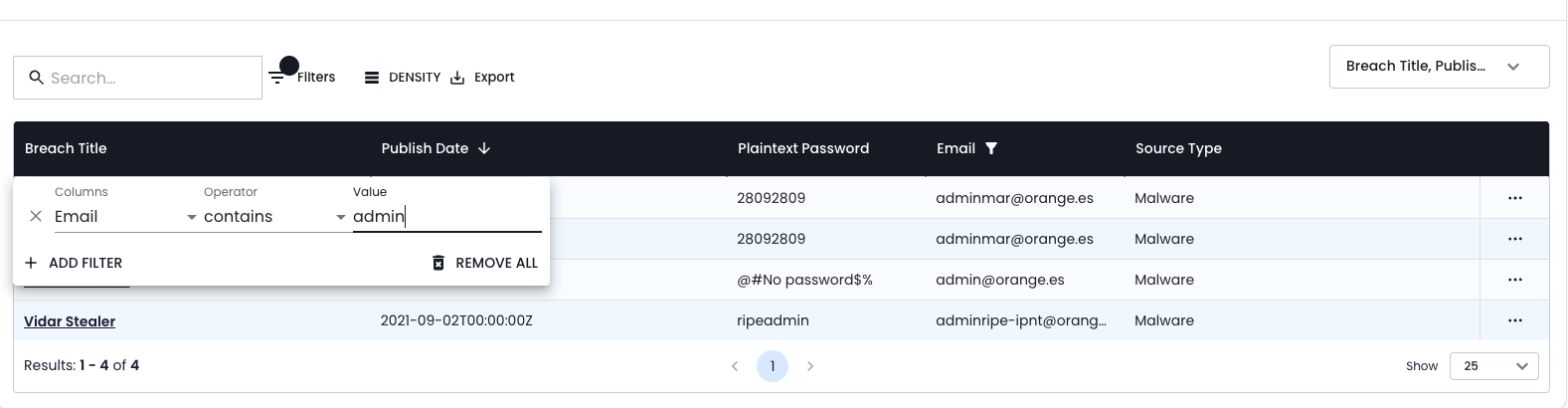
Key actions:
- SpyCloud filter:
- Field: Email
- Operator: Contains
- Value:
admin
- Identify high-risk accounts like
[email protected](linked to RIPE account access) - Flag for enhanced scrutiny and password resets
- Recommend MFA and lockdown procedures
👇ACCOUNT DETAILS
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
Step 3: Analyze the Infected Machine and User Context
Investigate the machine tied to adminripe-ipnt to determine legitimacy of the session.
Key indicators:
- Operating System: Windows 10 Pro (typical for corporate devices)
- IP Address: Located in Spain; no VPN/proxy
- Visited URL:
access.ripe.net— aligns with use of elevated credentials
Likely a real employee device that was infected.
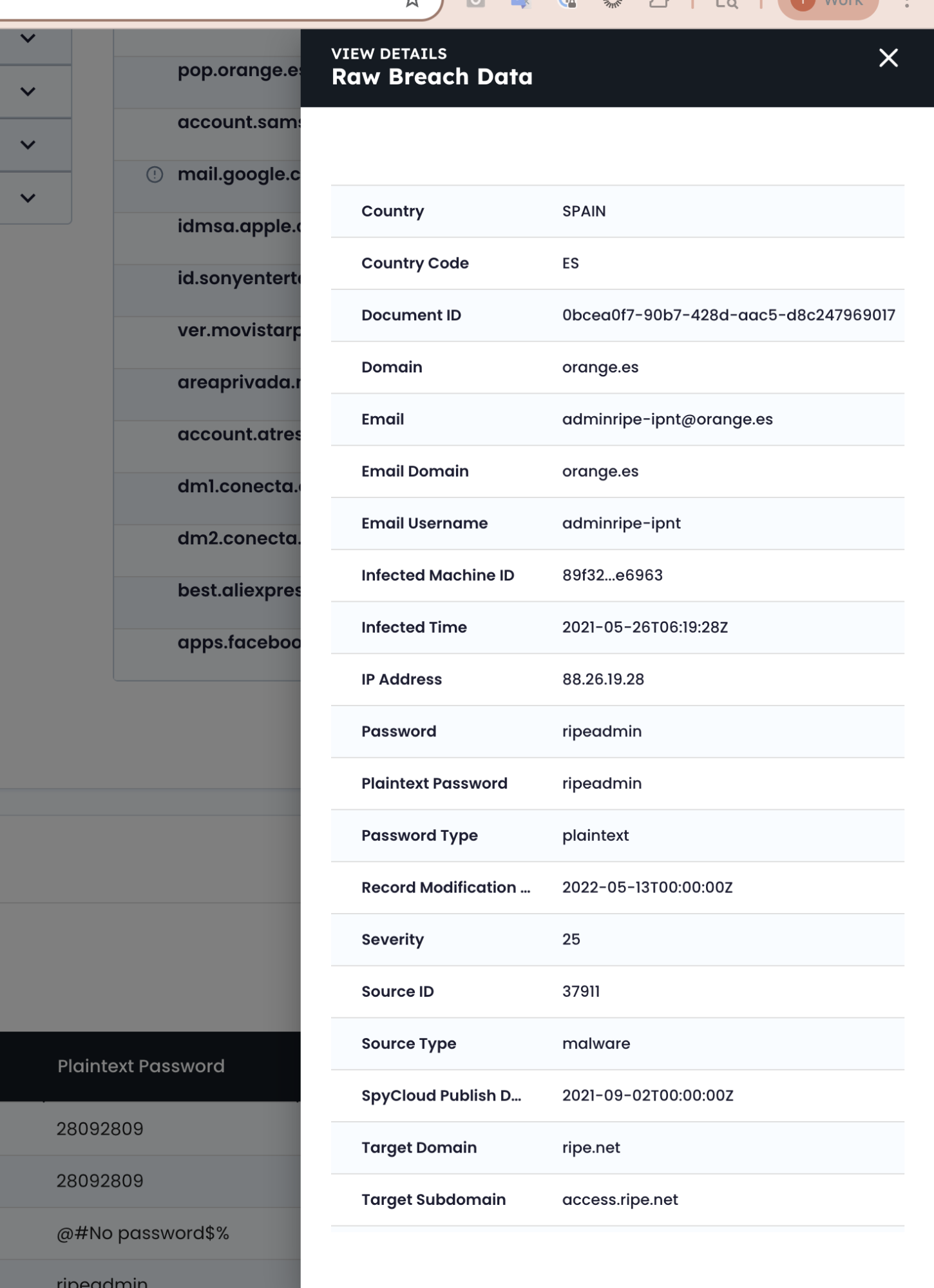
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
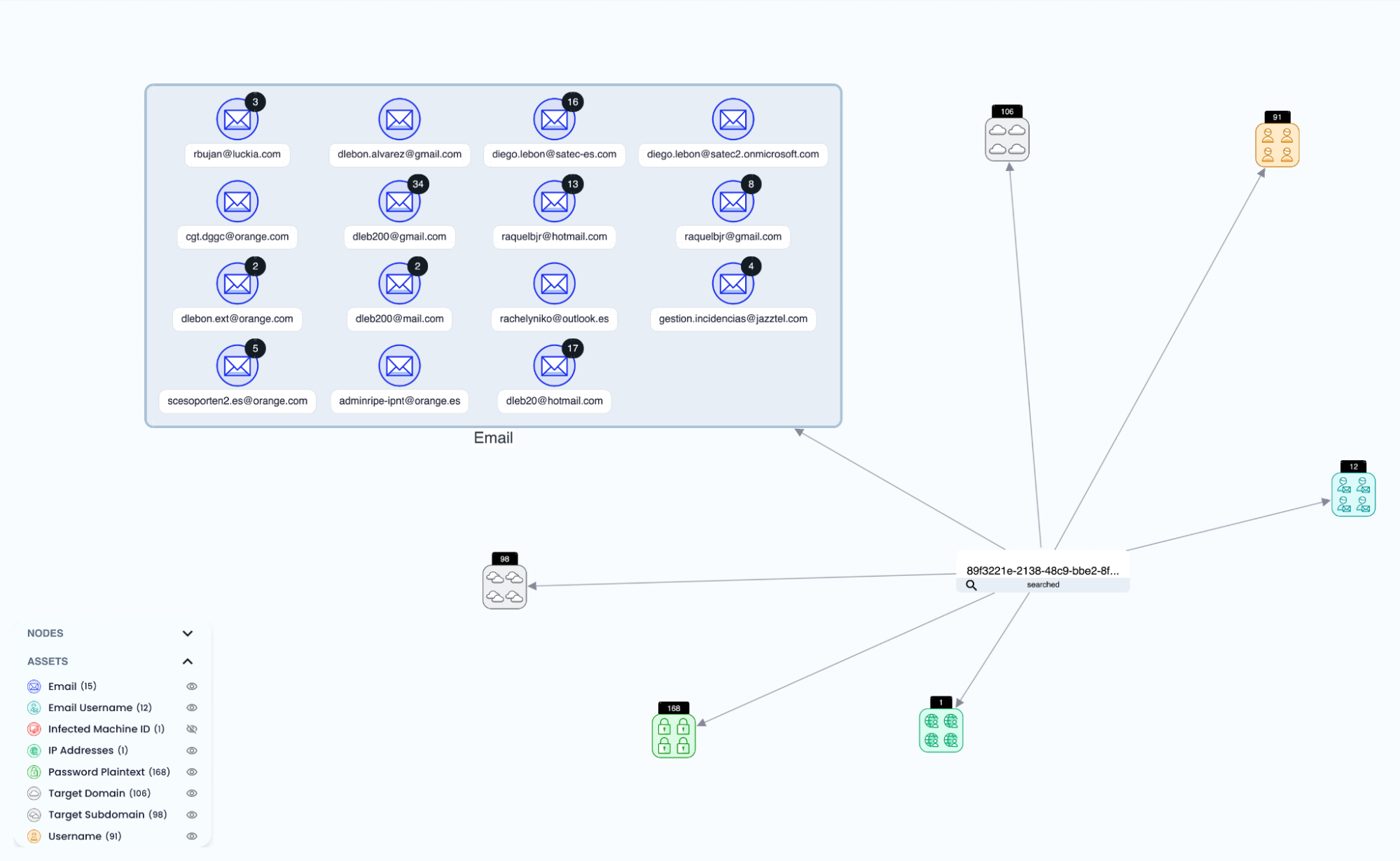
Step 4: Investigate Broader Activity From the Infected Machine
Query the Infected Machine ID:
89f3221e-2138-48c9-bbe2-8f68-806e6f6e6963
Key findings:
- Credentials from other organizations found on the device:
@satec-es.com(contractor email)[email protected][email protected]
Analysis:
- Device likely belongs to a SATEC contractor with elevated access
- Reinforces a supply chain exposure scenario
Response:
- Forensic review and containment of the device
- Notify and coordinate with SATEC and Orange security teams
👇GRAPH VIEW
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
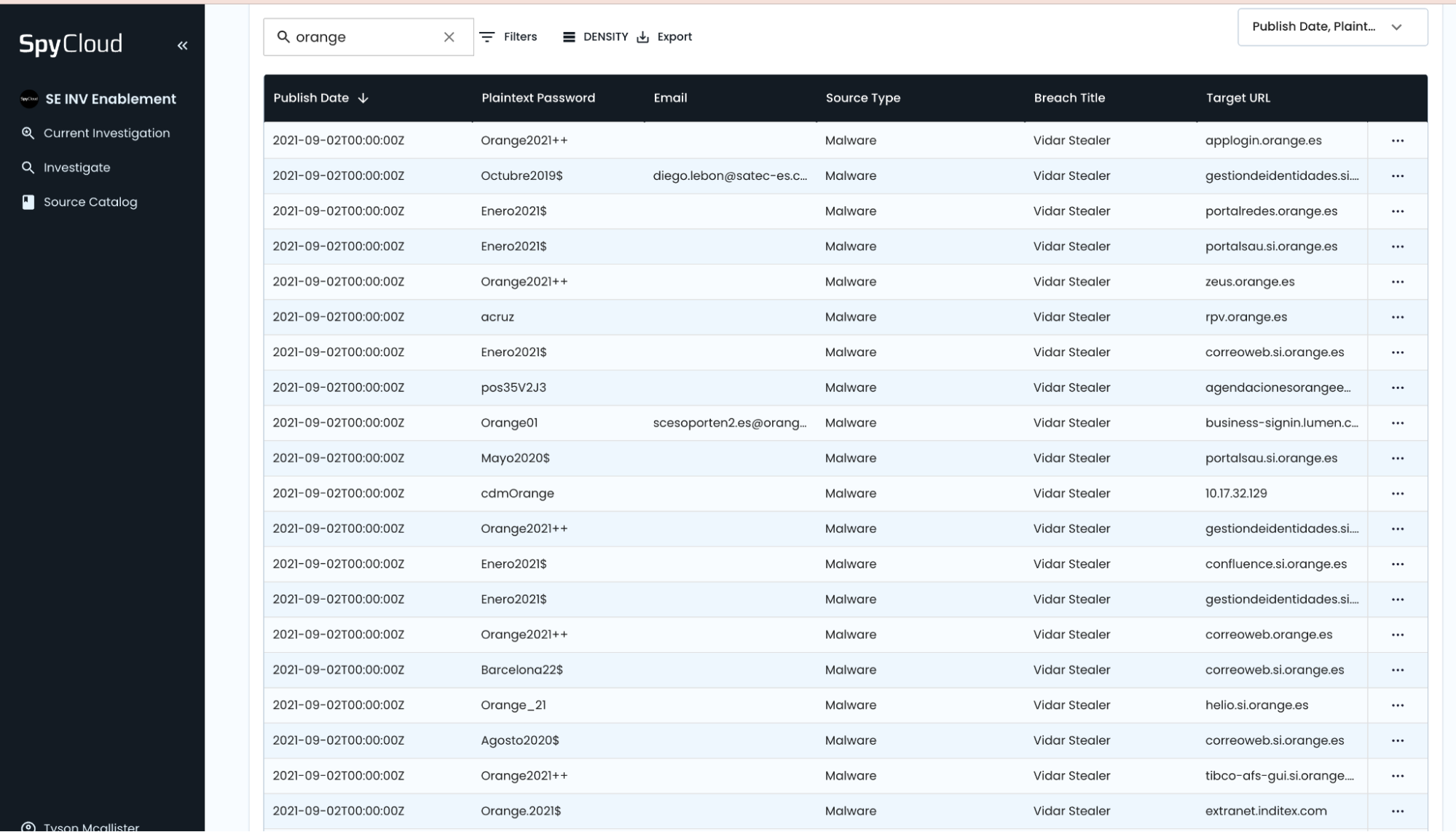
Step 5: Investigate Password Reuse Across Orange Accounts
Credential reuse significantly increases risk in third-party environments.
Key actions:
- Correlate passwords reused across:
@orange.es@orange.com@satec-es.com
- Detect crossover between contractor and internal users
- Flag any reuse across unrelated users or multiple breaches
Concerns:
- Shared credentials between entities
- Weak credential hygiene and separation
Remediation:
- Immediate password resets
- Enforce credential segmentation between orgs
- Notify vendor risk managers
👇 CONCERNS REFLECTED IN RESULTS
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
Next Steps
This concludes the first phase of the investigation.
- Map threat actor infrastructure
- Extract and share IOCs
- Integrate findings into SIEM/SOAR systems for automation
The examples featured in this guide are drawn from real-world breach data to showcase how SpyCloud AI Insights enhances identity investigations. They are intended to demonstrate product capabilities and reflect common patterns our platform uncovers in compromised identity ecosystems.
While based on actual breach intelligence, these case studies are provided for illustrative purposes only. SpyCloud does not make determinations about individual intent or behavior, and the inclusion of specific data points does not imply malicious activity.
Updated 4 months ago