Microsoft Defender for Endpoint
For SpyCloud Enterprise Protection.
🛡️ Enterprise Protection for Microsoft Defender for Endpoint
Use SpyCloud’s post-infection identity evidence to surface compromised endpoints and the credentials, cookies, and tokens criminals can abuse – then contain and remediate quickly in Microsoft Defender for Endpoint.
Integrations page: https://spycloud.com/products/integrations/microsoft-defender/
Why this matters: SpyCloud Labs found 66% of infostealer-infected devices already had endpoint security installed at compromise – identity artifacts still leaked and can be abused.
🚀 Benefits at a glance
- ⏱️ Accelerate Response – Reduce MTTD/MTTR by acting earlier in the attack lifecycle.
- 🧪 Enhance Detection – Catch infostealer malware that bypasses EDR, including infections on unmanaged devices.
- 🧯 Prevent Lateral Movement – Isolate compromised endpoints to block ransomware entry points.
🧭 How it works
1) Detect – post-infection identity evidence
SpyCloud continuously detects newly recaptured identity records stolen by infostealer malware (e.g., plaintext creds, cookies/tokens) and identifies impacted users/devices.
2) Decide – policy-driven response
Choose actions that fit your playbooks: alert only, or immediately isolate devices, reset/revoke, and notify users/owners.
3) Act – contain & remediate in MDE
Trigger endpoint isolation, live response, or script execution for rapid cleanup and credential/session hygiene.
4) Prove – measure outcomes
Use daily reports and exports to show exposure volume, time-to-contain, and remediation throughput.
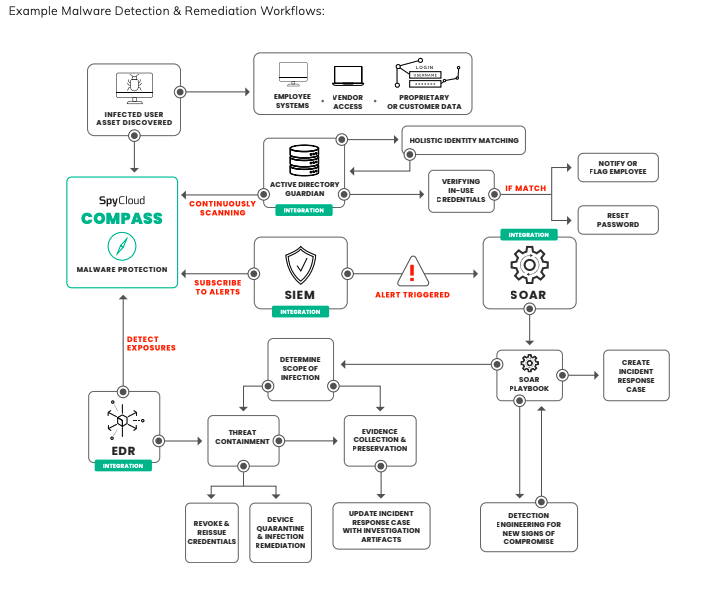
🧰 Key capabilities
- 📬 Daily reports – Lists compromised endpoints + identity data (hostnames, usernames, IPs, infection timestamps).
- 🔔 Flexible alerting – Route alerts to Slack, Jira, or email to fit existing workflows.
- 🛡️ Customizable containment – Automate isolation or require manual review – your rules.
- ⚙️ Simple setup – UI-driven configuration with Defender-compatible options.
- 🕒 Custom time range – Search the last 24 hours or expand the timeframe as needed.
- 💻 Live script execution – Remotely trigger scripts on Defender-managed devices to accelerate IR.
🛠️ Technical requirements
- Microsoft Defender for Endpoint P2
- API permissions (MDE):
Machine.Read.All– read device informationMachine.Isolate– remote endpoint isolationMachine.LiveResponse– live response session actionsMachine.LiveResponse.Read– read live response results
- MDE features enabled:
- Device Read Access
- Device Isolation
- Live Response Actions
- Live Response Result Retrieval
- SpyCloud Compass license + SpyCloud Enterprise API key
🧯 Containment & remediation (in practice)
- Contain: isolate compromised endpoints from internal resources while keeping Defender cloud access for remediation.
- Remediate: reset exposed passwords, revoke sessions/tokens, and force re-auth for affected users.
- Notify: inform users/owners; ticket for auditability.
✅ Expected outcomes
- Higher-fidelity detections of identity-based threats from infostealer infections
- Faster containment and reduced exposure window for workforce identities
- Operational proof of improved time-to-response via reports/exports
Updated 29 days ago