Tines SOAR
For SpyCloud Enterprise Protection.
🤖 Enterprise Protection + Tines
Use SpyCloud’s recaptured darknet exposure data – from breaches, malware-infected devices, and successful phishing – to automate response with Tines. Generate cases, triage by source/severity, and run policy-driven playbooks to reset credentials, revoke sessions, notify users, and more.
Integrations page: https://spycloud.com/products/integrations/tines/

🚀 What you get (at a glance)
- Ingest SpyCloud exposure records (breach, malware, phished) into Tines
- Pre-built, customizable templates to jump-start automation
- Granular triage by source/severity to focus on the highest-risk users first
- Case management: auto-generate new cases when matching exposure records are detected
- Proactive notifications (e.g., Slack/email) for high-impact events
Outcome: Shorter exposure windows and repeatable, low-friction response – straight from Tines.
🧭 Quick start
- Choose a SpyCloud template in Tines to start your Story
- Add your SpyCloud API key to begin ingesting exposure data
- Automatically ingest exposures (breach, malware, phished) tied to employee identities and route to cases/notifications
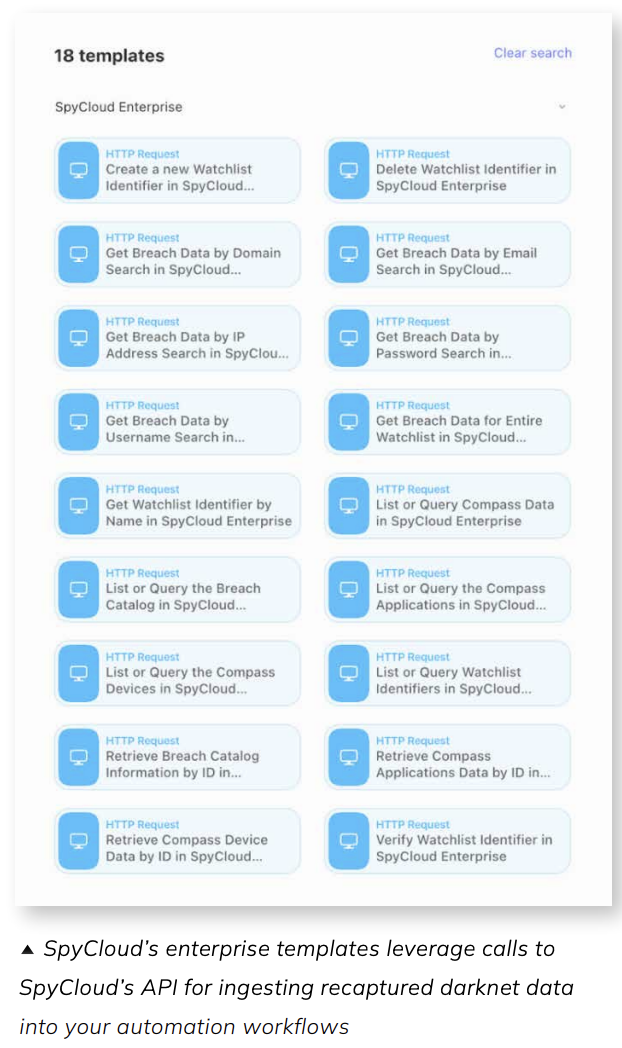
🧱 Templates & Stories
Kick off with SpyCloud starter templates in Tines and extend as needed:
- Create separate paths per source (breach vs. malware vs. phished)
- Enrich with local context (IdP, HRIS, EDR, IAM)
- Branch by severity and artifact type (plaintext credentials, cookies/tokens, etc.)
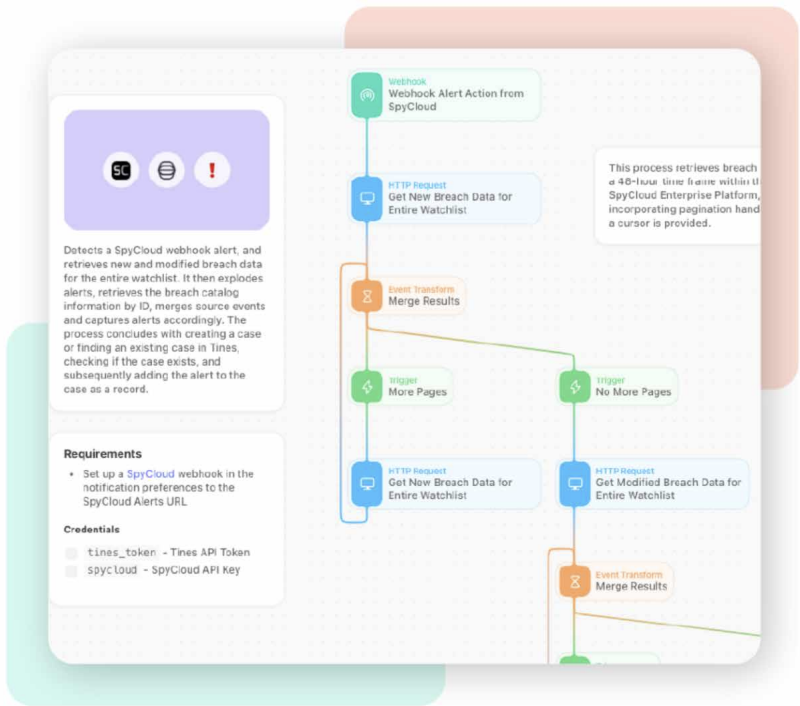
🔧 Common use cases
- Tailored response – Remediate exposed employee or customer credentials with the specific steps your policy requires
- Granular triage – Segment SpyCloud notifications by breach, malware, and phished sources; prioritize Critical/High first
- Case management – Detect new SpyCloud exposure records and auto-create cases in Tines (only if not already present)
- Proactive notification – Alert users (Slack/email) when a new exposure is surfaced for their identity
🛠️ How it works (expand to see steps)
1) Ingest – bring SpyCloud exposure data into Tines
Use the SpyCloud templates to pull exposure records sourced from breaches, malware infections (infostealer logs), and phished credentials into Tines.
2) Triage – sort by source & severity
Route by exposure source (breach/malware/phished), severity (e.g., Critical/High), and artifact type (plaintext password, cookies, tokens) to determine next actions.
3) Act – run playbooks
Automate remediations: reset credentials, revoke sessions, force re-auth, disable accounts, and notify end-users or admins.
4) Prove – document & measure
Create/update cases, track outcomes, and export metrics that show time-to-response and volume of exposures remediated.
📚 Resources
- SpyCloud Enterprise Protection APIs – use for flexible ingestion & enrichment
- Tines Story Library – browse/import automation templates here
- Contact SpyCloud – to enable additional datasets or discuss policy/IR playbooks
Want to do more with Tines + SpyCloud? See all stories here
✅ Summary
- One integration to ingest & act on breach/malware/phished exposures
- Templates to move fast; Stories to customize deeply
- Automated, measurable remediation that shrinks your identity exposure window
Updated 29 days ago