Investigating Fraud
ANALYST HIGHLIGHTS USING SPYCLOUD INVESTIGATIONS MODULE
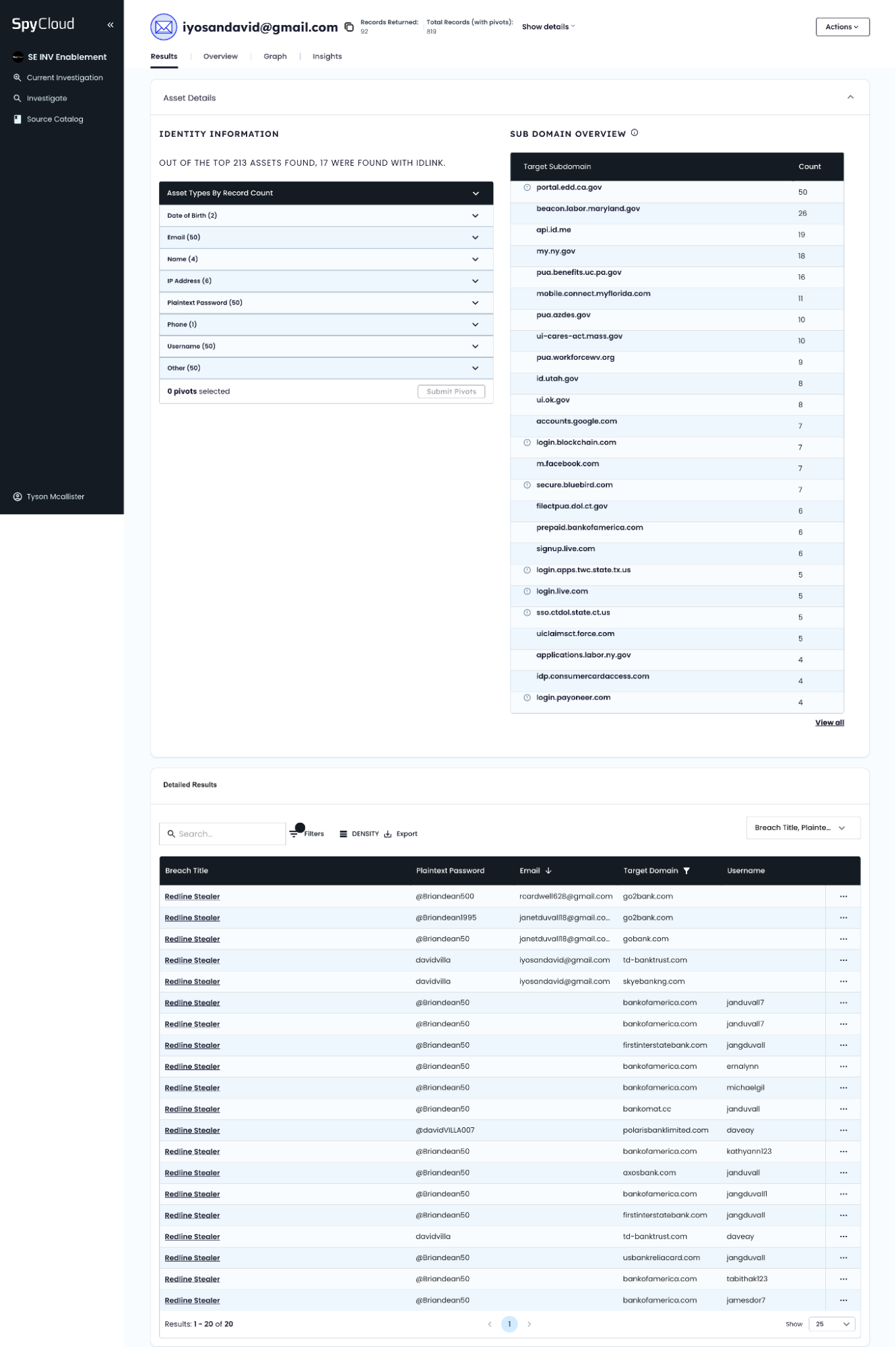
Investigation into [email protected]
[email protected]Primary Identity
- Email:
[email protected] - Found on infected host (Redline Stealer)
- Machine geo-located in Nigeria
- Reused across multiple logins; usernames include:
davdvilla,@Brkndan50,janduvall7
What to Look For
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
1. Multi-State Unemployment Fraud
- Targeted domains include:
portal.edd.ca.gov(California)beacon.labor.maryland.govmy.my.govpua.workforcewv.org,mobile.connect.myflorida.com, etc.
- Access pattern suggests mass-application across states
- Indicators to monitor:
- Same IP/device used across multiple state systems
- Reused PII data (SSN, DOB, name, etc.)
- Unusual claim submission timing or volume
2. Bank and Prepaid Card Access
- Targets:
bankofamerica.com,td-banktrust.com,gobank.comsecure.bluebird.com(American Express prepaid)firstinterstatebank.com,prepaid.bankofamerica.com
- Investigate for:
- Account takeovers or new fraudulent account creation
- Linking of stolen identities to mule accounts
- Shared credentials or device fingerprints
3. Cryptocurrency and Payment Services
- Accessed:
login.blockchain.com,login.payoneer.com
- Flags:
- Potential laundering of stolen funds via crypto
- Use of platforms with limited KYC for quick transfers
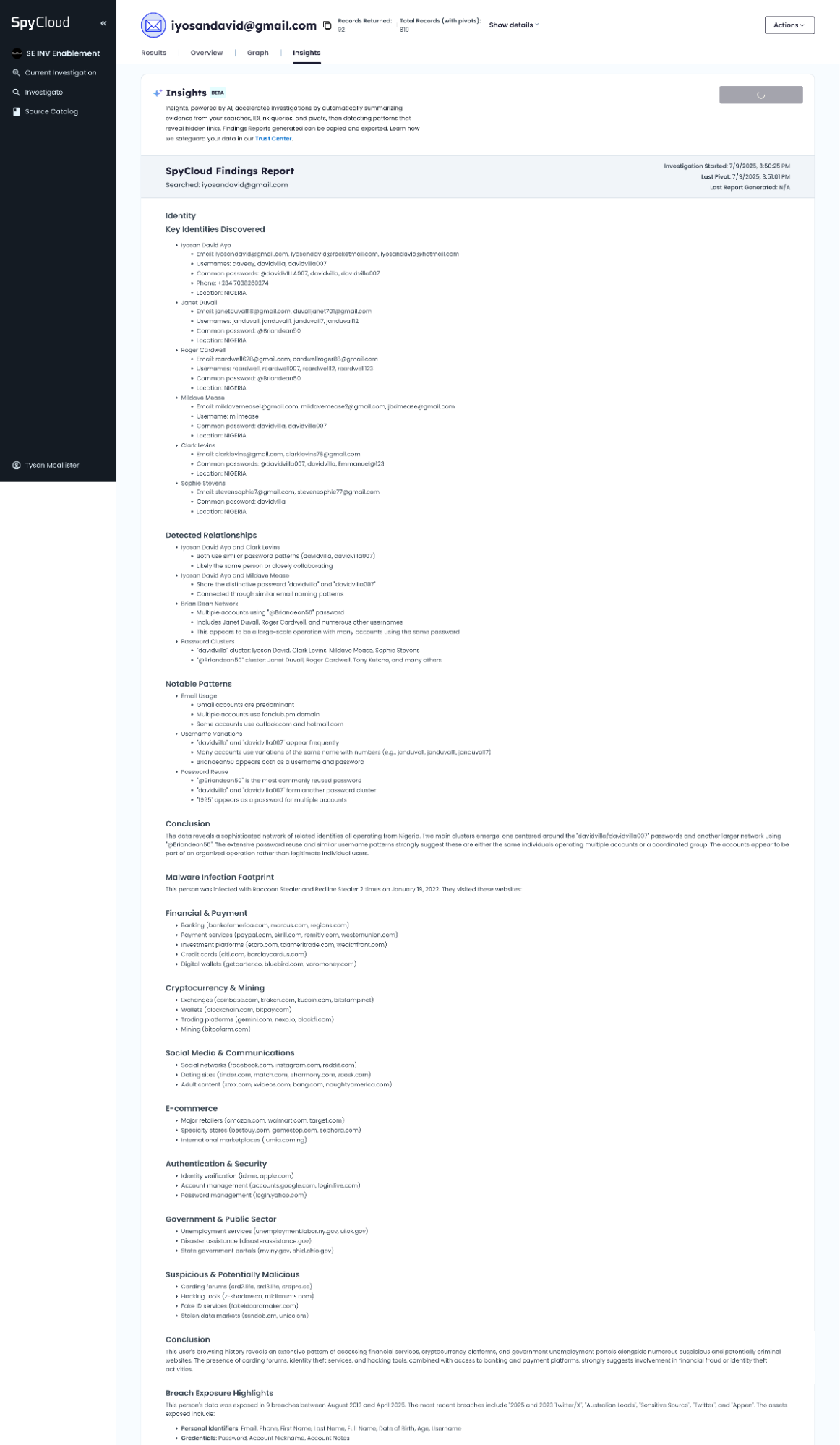
Browsing History = Malicious Intent
- History shows deliberate access to:
- Carding and identity theft forums
- Fake document and SSN services
- Malware/toolkit panels (e.g., Redline, Raccoon)
Strong indication that this is not a passive victim, but an active participant in fraud.
Example shown for demonstration purposes only. No assumptions should be made about individual behavior or intent.
Pivot Opportunities
- Look for reuse of:
- Passwords (e.g.,
@Brkndan50) across services - Emails or aliases across other datasets
- Device fingerprints, session cookies, or browser artifacts
- Passwords (e.g.,
- GeoIP matches to Nigerian IPs across fraud attempts
- Cross-reference banking or crypto logins tied to exposed credentials
Summary for Triage
This case shows strong indicators of organized financial fraud activity.
The infected device in Nigeria, combined with access to identity theft tools, multiple benefit portals, and banking infrastructure, aligns with known tactics of West African fraud networks.
This user should be prioritized for deeper linkage and infrastructure mapping.
The examples featured in this guide are drawn from real-world breach data to showcase how SpyCloud AI Insights enhances identity investigations. They are intended to demonstrate product capabilities and reflect common patterns our platform uncovers in compromised identity ecosystems.
While based on actual breach intelligence, these case studies are provided for illustrative purposes only. SpyCloud does not make determinations about individual intent or behavior, and the inclusion of specific data points does not imply malicious activity.
Updated 6 months ago