Crowdstrike Falcon EDR
For SpyCloud Compass.
🛡️ Enterprise Protection for CrowdStrike Falcon (EDR)
Malware-infected devices are a launchpad for identity-based threats: plaintext credentials, cookies, and tokens can be siphoned from endpoints and abused for ATO, session hijacking, and lateral movement. SpyCloud + CrowdStrike Falcon delivers the post-infection identity evidence your SOC needs to find compromised users and remediate fast – even when malware bypasses EDR or lands on unmanaged devices.
Integration page: https://spycloud.com/products/integrations/crowdstrike-falcon/
SpyCloud Compass license is required to use this integration with Crowdstrike Falcon EDR.
🚀 What you get
- Post-infection visibility: See compromised endpoints and the identity artifacts criminals can exploit (credentials, cookies/tokens).
- Detect bypass & blind spots: Identify infostealer malware that evaded EDR or infected unmanaged devices outside corporate control.
- Automated containment: Isolate compromised endpoints and block ransomware entry points via Crowdstrike Falcon policies.
- Operational workflows: Route alerts and cases to Slack, Jira, email, or your IR tooling for repeatable remediation.
Bottom line: reduce MTTD/MTTR by acting on reliable identity evidence – not just process or network heuristics.
🧭 Quick start
- Connect SpyCloud post-infection identity data to Crowdstrike Falcon (via your established ingest/automation method).
- Validate detections by listing compromised endpoints and matched identity artifacts (hostnames, usernames, IPs, timestamps).
- Create policies/playbooks to quarantine endpoints, revoke sessions, and reset exposed credentials.
- Automate notifications (Slack/Jira/email) and ticketing to keep owners and responders aligned.
🔎 Investigate & act on real evidence
Focus on the identity signals that matter most:
- Plaintext or previously exposed credentials tied to the infected host/user
- Malware-sourced session artifacts: cookies/tokens enabling account abuse
- Indicators of reuse/variations attackers can easily guess
Use Crowdstrike Falcon to:
- 🔍 Locate impacted endpoints/users and pivot into host telemetry
- 🧩 Correlate SpyCloud identity evidence with detections, process trees, and network activity
- 🧯 Contain quickly: isolate endpoints, expire tokens, reset passwords, and enforce re-auth
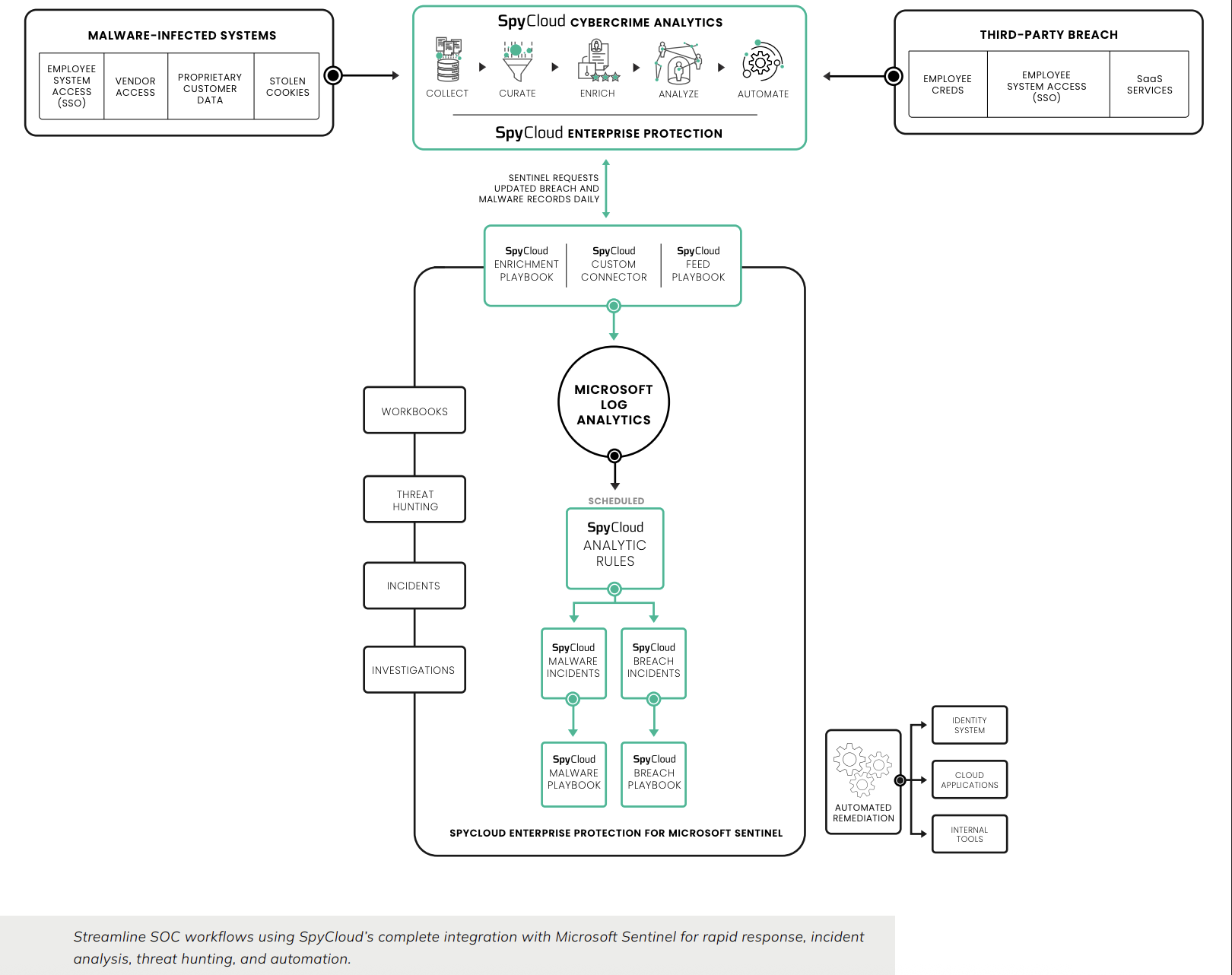
🛠️ How it works
1) Detect – identify malware-infected devices & exposed identities
SpyCloud surfaces evidence from malware-infected devices (infostealer logs). This includes plaintext credentials and session artifacts that criminals actively resell and reuse.
2) Enrich – tie identity artifacts to endpoints/users
Match credentials, cookies, and tokens to your users and Falcon-managed hosts to understand blast radius and prioritize.
3) Contain – isolate & block
Use Falcon policies to isolate compromised endpoints and block further data exfiltration or lateral movement.
4) Remediate – reset & revoke
Reset exposed passwords, revoke sessions/tokens, and force re-authentication. Notify users and owners via Slack/Jira/email.
📊 Validation & reporting
- Confirm compromised endpoint lists and identity matches are populating as expected
- Track containment time, reset/revoke counts, and endpoint quarantine rate
- Trend infection sources and identity artifact types (password vs. cookie/token)
Tip: Pair Crowdstrike Falcon’s response telemetry with SpyCloud’s identity evidence for clear “before/after” reporting.
🔗 Resources
- Integration page: https://spycloud.com/products/integrations/crowdstrike-falcon/
- Demo video: https://spycloud.com/products/integrations/crowdstrike-falcon/?wvideo=ta2xioxzov
✅ Expected outcomes
- Faster containment of malware-infected devices and identity abuse
- Fewer blind spots (catch infections that bypass EDR or occur on unmanaged hosts)
- Reduced exposure window for workforce identities; measurable MTTD/MTTR improvements 📸 Image placement map (exact slots)
▶️ Demo
Updated 29 days ago