Understanding Alerts & Severity
WITHIN SPYCLOUD COMPASS
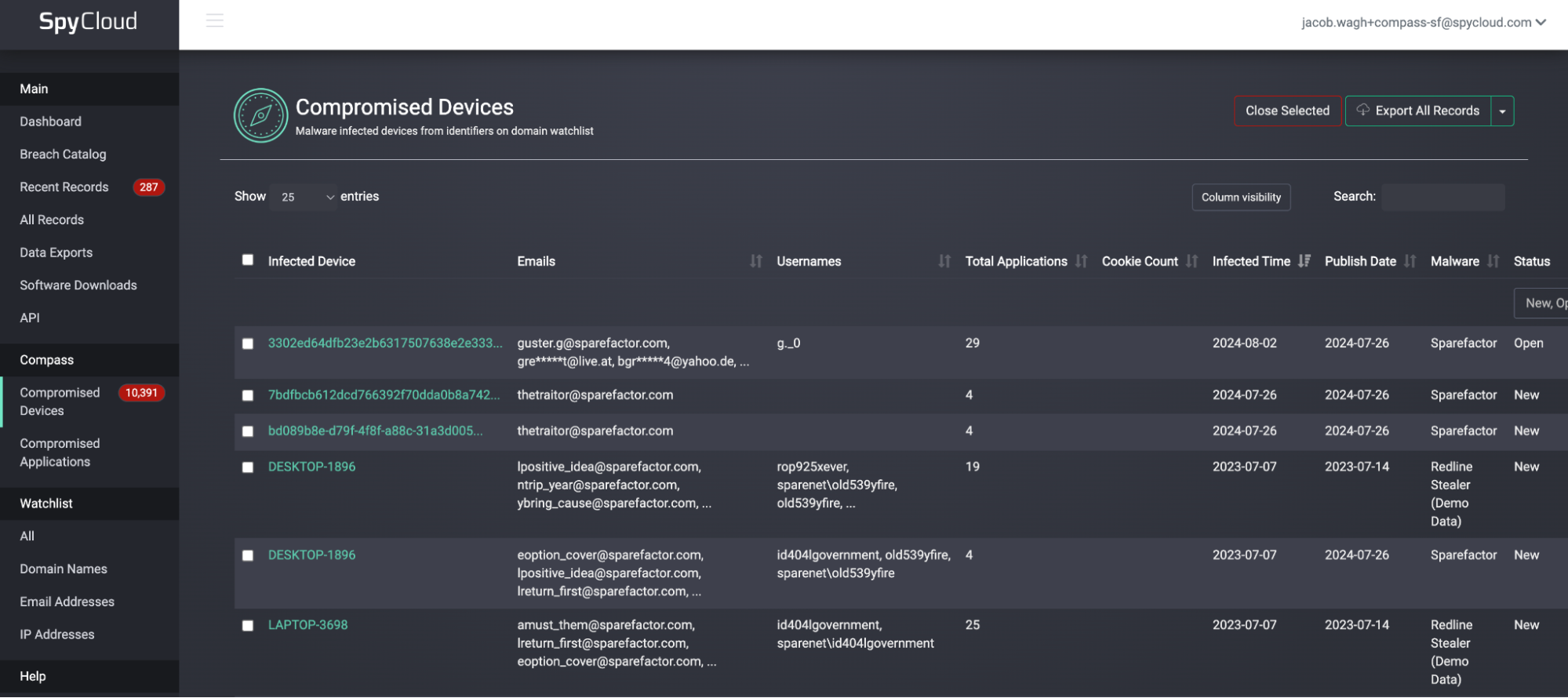
🖥️ Step 1: View Infected Device List
Start by reviewing the Compromised Devices dashboard.
- Devices are sortable by alias, email, IP, and source type.
- Click the hostname to investigate further and launch the Device Graph.
👇 INFECTED DEVICE LIST
You can view the detail panel for a specific device
**👇DEVICE DETAIL **
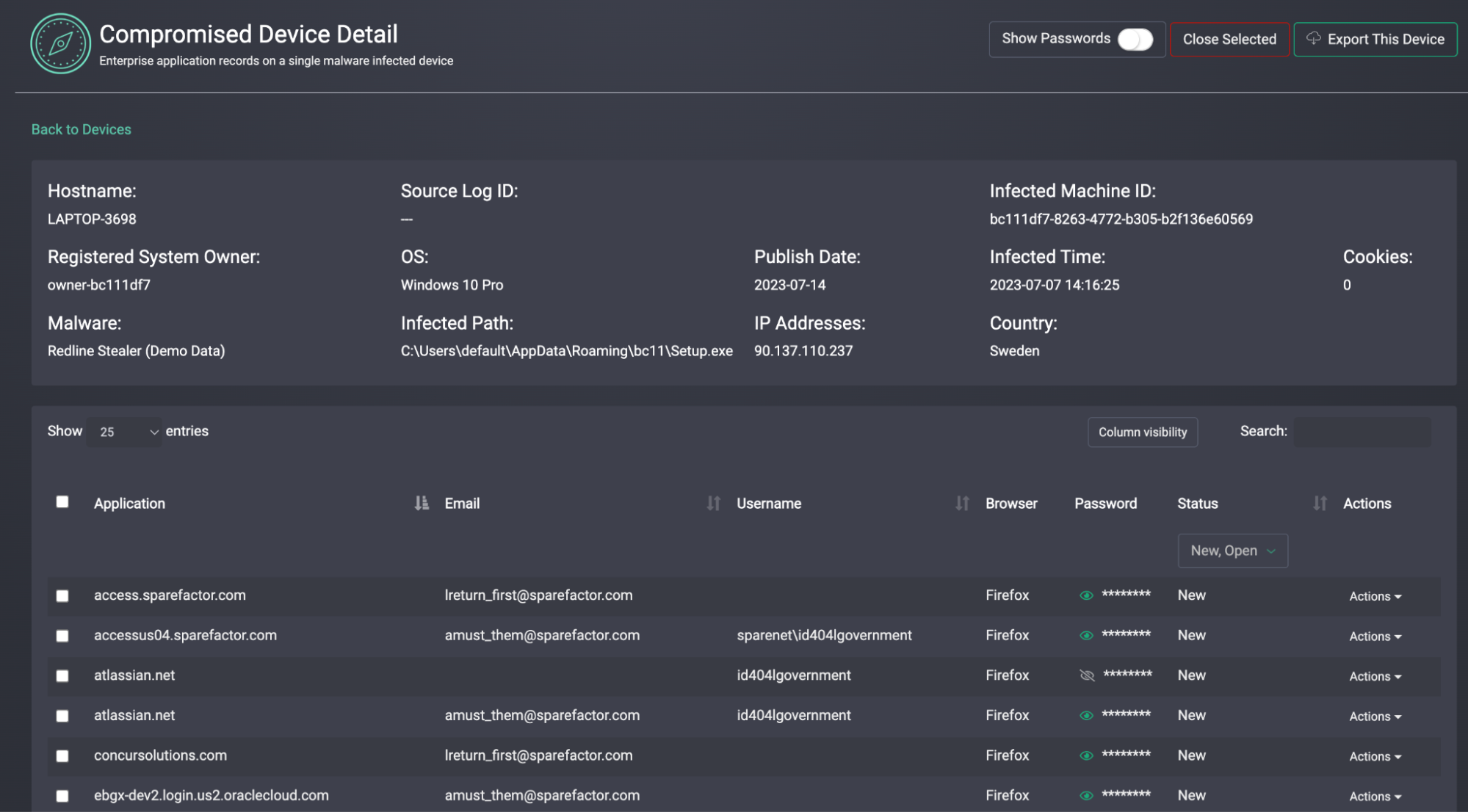
👤 Step 2: Correlate Employee Status
Cross-check exposed identities (e.g., [email protected]) against internal HRIS or directory data.
Compass alerts show:
- Domains involved (internal vs third-party)
- Selector types (email, IP, password, app login)
- Historical matches and risk scoring
🧠 Compass Alert Severity
Each alert is assigned a severity from 5 (low) to 25 (high), based on:
- Source type (malware > phish > breach > combolist)
- Password status (cracked, reused, plaintext)
- Domain match (does it match your monitored assets?)
- Recency and exposure depth
| Severity | Meaning |
|---|---|
| 2 | Email only - typically from a breach or phishing target list |
| 5 | Informational - could contain sensitive data, but no plaintext password |
| 20 | Credential with plaintext password, could contain sensitive data. |
| 25 | Malware log with credentials, infected machine info, and/or behavioral signals |
| 26 | Session cookie data taken from a device infected by malware |
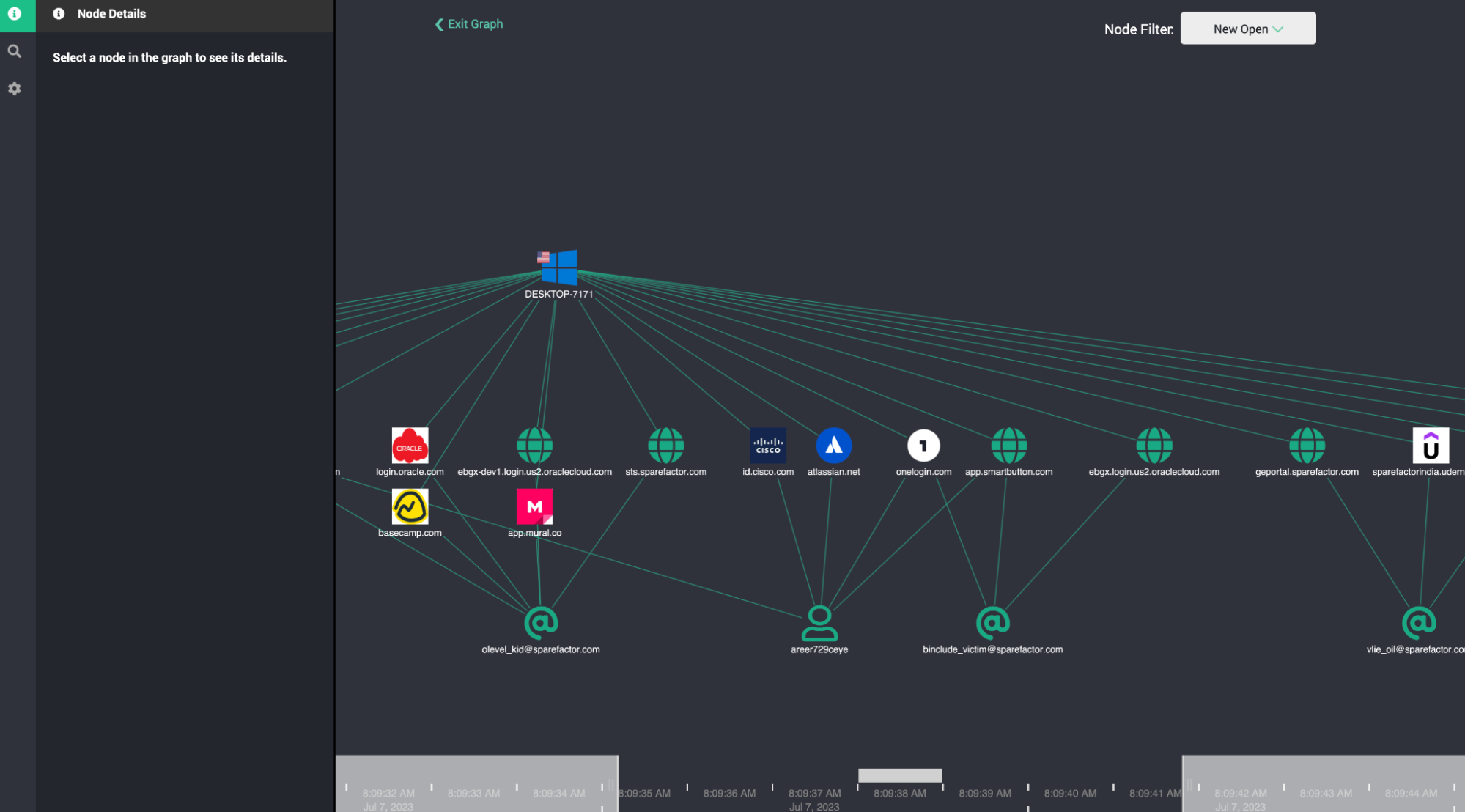
🧩 Step 3: Explore the Device Graph
Open the interactive graph to explore connections:
- Click any node (email, login, device, domain)
- Pivot across selectors and linked accounts
- Review compromised assets and exposure type
👇DEVICE GRAPH
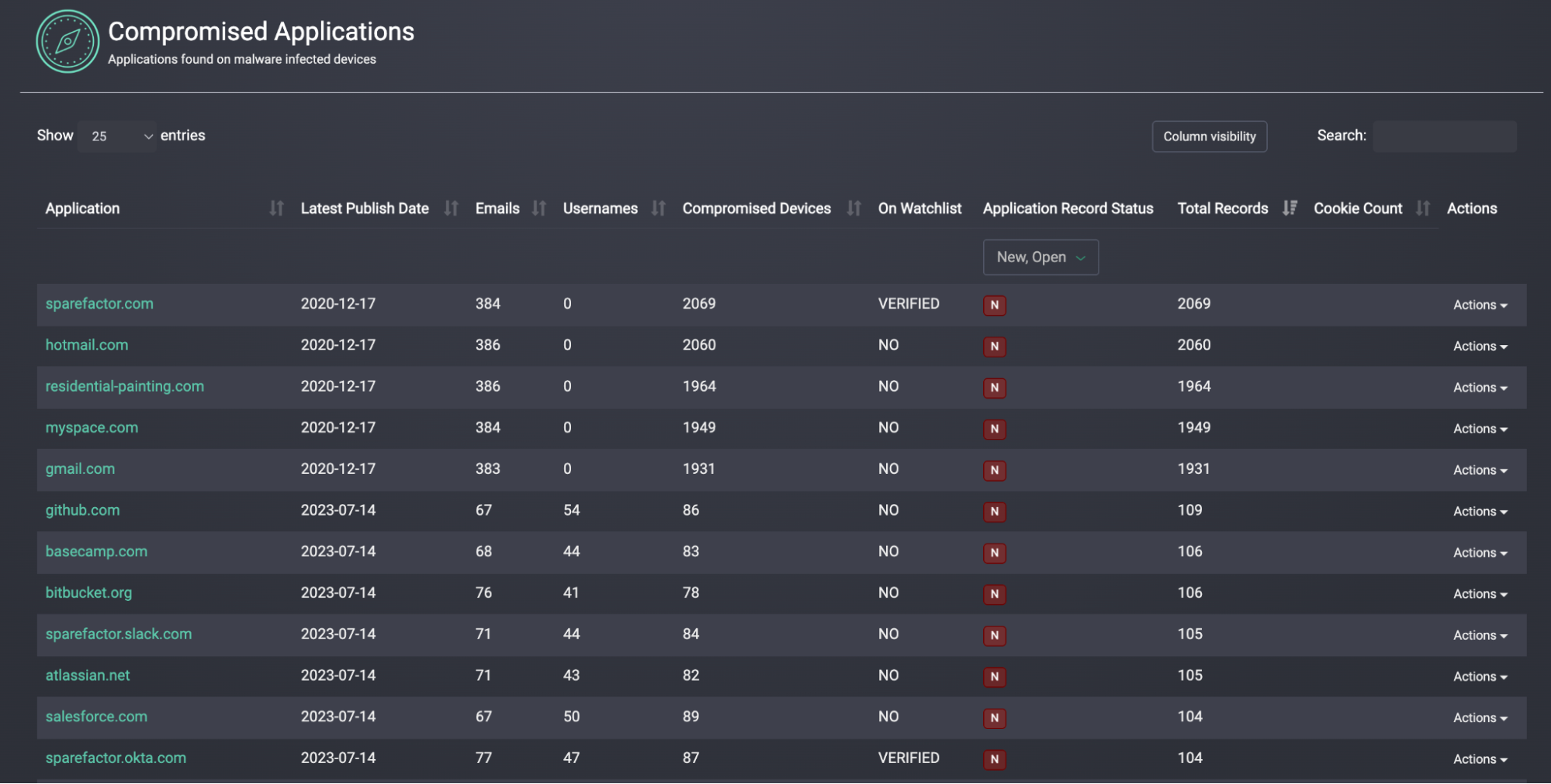
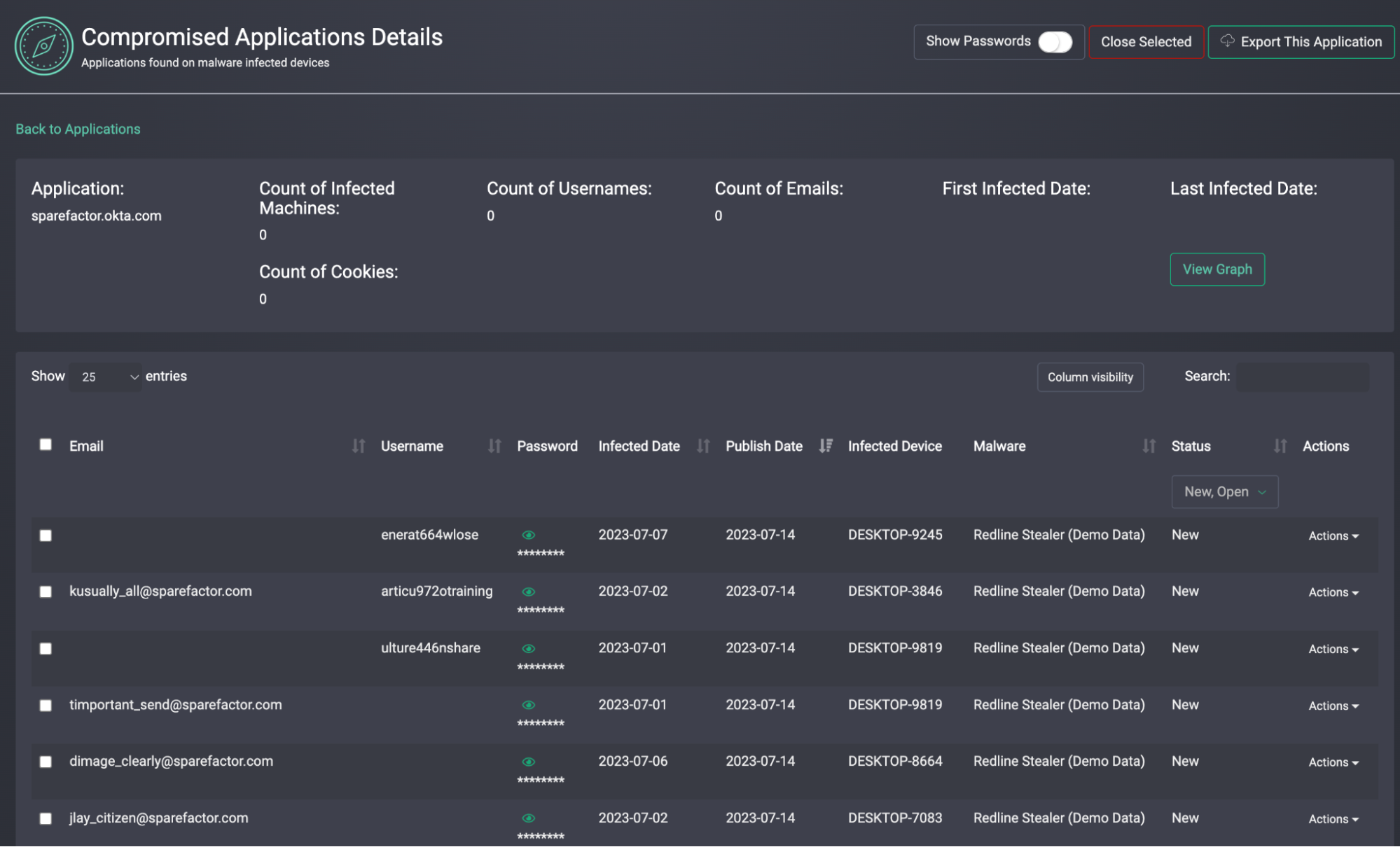
💻 Step 4: Review Exposed Applications
- Compass surfaces all logins to enterprise applications from the infected device.
- Easily identify high-risk app access.
- Add any new subdomains (e.g., internal tools) to your monitoring list.
👇COMPROMISED APPLICATION VIEW
🔧 Step 5: Recommended Remediation Actions
Based on alert score, metadata, and device context, follow these steps:
- 🛑 Notify and isolate the user/device via EDR, MDM, or helpdesk.
- 🔐 Rotate passwords for exposed logins or domains.
- 🧾 Review access logs in your IdP, SIEM, or app telemetry.
- 💻 Reimage the device or perform targeted cleanup.
- 🌀 Repeat for any linked app accounts.
👇POST-INFECTION RESPONSE STEPS
🧠 Tip: Start with What You Can Automate
Compass risk scoring and metadata are ideal for:
- Feeding SOAR playbooks
- Prioritizing human triage
- Auto-generating IT tickets based on severity
Check out Responding & Remediation for automation examples and integrations.
Updated 4 months ago