The "Before You Get Started" Guide
For SpyCloud Consumer ATO Prevetion.
🚀 Before You Get Started with Consumer ATO Prevention (CAP)
SpyCloud’s Consumer ATO Prevention (CAP) helps you prevent consumer account takeover by detecting exposed credentials before they’re abused. This guide covers planning, collaboration, integration patterns, and how to measure success.
📝 Getting Started
Planning Your Implementation
- Gather requirements early.
- Identify all teams that need to be involved.
- Ensure devs are familiar with SpyCloud APIs (see Portal).
- Verify access permissions for all stakeholders.
- Build in time for testing and iteration.
🤝 Preparing to Collaborate with Other Teams
💡 Build a Business Case
- Outline the opportunity cost of delay:
- Number of accounts taken over
- Average fraud loss per incident (direct $ + wasted cycles/opportunity cost)
- If data is hard to obtain, use representative cases to illustrate impact.
✨ Address Customer Experience
- Explain measures to avoid friction (asynchronous checks, fail-open at login).
- Share attention-grabbing stats (e.g., “X% of customer passwords appear in SpyCloud data”).
📣 Keep Stakeholders Engaged
- Report outcomes regularly: accounts protected, fraud averted, reduction in escalations.
- Maintain alignment with product, CX, finance, and leadership.
🔑 Implementation: Common Approaches
Enterprises typically call SpyCloud APIs at the following points:
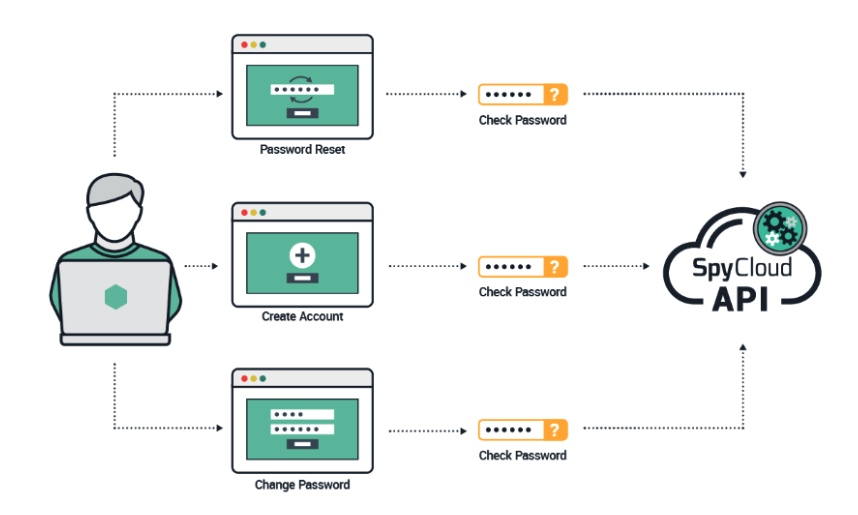
🔒 Password Creation
- Call Password Exposure API on create / reset / change.
- Use exposure counts to block weak/known-bad passwords.
- Calibrate thresholds by risk:
- High-value (finance): block if seen even once.
- High-friction-risk (ecom): block only the most common.
- Optionally cap failed attempts to reduce churn.
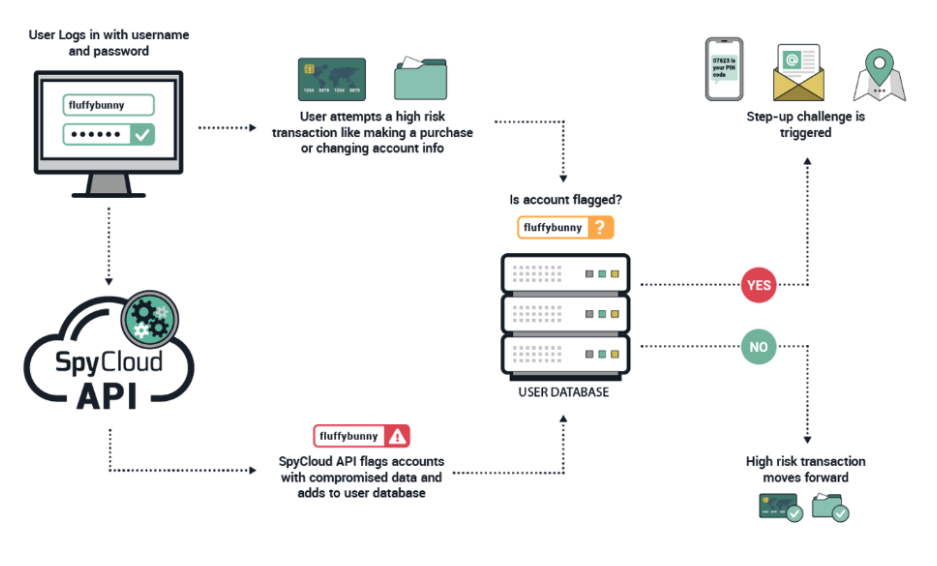
✅ Login
- Call User Exposure API asynchronously at login.
- Fail open so errors don’t block legitimate users.
- If exposed, flag the account and require step-up auth for risky actions:
- Multi-factor authentication (MFA)
- Email verification
- Geolocation or other behind-the-scenes checks
- Optionally force a password reset later to minimize login friction.
🔁 Password Reset
- Check newly provided credentials during reset.
- Prevent users from resetting into compromised passwords.
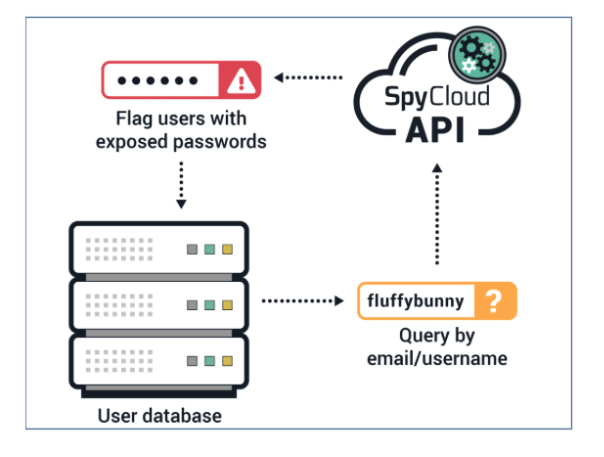
📦 At Rest (Batch Mode)
- Run scheduled checks of your entire user base (nightly → monthly).
- Detect exposures for dormant or inactive users.
- Schedule during low-volume windows.
🛡️ Account Maintenance & Ongoing Protection
⏱️ Continuous Exposure Monitoring
Run scheduled checks (daily, weekly, or monthly) against SpyCloud’s dataset to identify newly compromised credentials associated with existing accounts. This ensures you’re not only reacting during login or reset events, but also proactively catching dormant accounts or infrequent users who may still pose a risk.
🧹 Credential Hygiene Enforcement
- Establish policies that trigger remediation workflows when SpyCloud flags an exposure. For example, force password rotation, revoke active sessions, or apply step-up authentication until the user resets credentials.
📩 Silent Notifications & Guided Recovery
- Instead of only enforcing disruptive resets, some organizations silently monitor and guide remediation: send tailored alerts, provide self-service recovery options, or encourage users to enable MFA if their credentials have been compromised.
💤 Inactive & Dormant Accounts
- Use SpyCloud data to identify exposures tied to accounts that haven’t logged in for months (or years). Decide whether to disable, flag, or place those accounts into a limited state until the user re-engages securely.
🕵️ Fraud & Risk Engine Integration
- Enrich broader fraud prevention or identity risk scoring systems with SpyCloud’s compromise signals, so exposed accounts can be flagged for higher scrutiny during future transactions or logins.
Updated 29 days ago