Microsoft Sentinel SIEM
For SpyCloud Enterprise Protection
🧩 Enterprise Protection for Microsoft Sentinel
Bring SpyCloud’s recaptured darknet exposure data – from breaches, malware-infected devices, and successful phishing – into Microsoft Sentinel to speed detection, investigation, and response for identity-based threats (ATO precursors, session hijacking, risky users).
Integration page: https://spycloud.com/products/integrations/microsoft-sentinel/
🚀 What you get (at a glance)
- Direct ingest of SpyCloud breach / malware / phished exposure data into Microsoft Sentinel
- Decrease MTTR with normalized, enriched identity evidence you can search, visualize, and alert on
- Create high-priority incidents automatically for new exposure events tied to your workforce
- Investigate at scale: query, pivot, and trend identity exposures across your environment
Result: clearer signal on who (the exposed user) and what (credentials, cookies, tokens), from breach + malware + phished sources – and faster, automated response.
🧭 Quick start
- Connect SpyCloud data to Microsoft Sentinel (data connector / ingest).
- Validate ingestion with a workbook or basic queries (see Dashboards & visuals).
- Create analytics rules for new/high-risk exposures (plaintext credentials, infected sessions, phished accounts).
- Automate handoffs via Logic Apps/Playbooks (reset creds, revoke sessions, force re-auth, notify users).
- Track trends and MTTR with dashboards/KPIs.
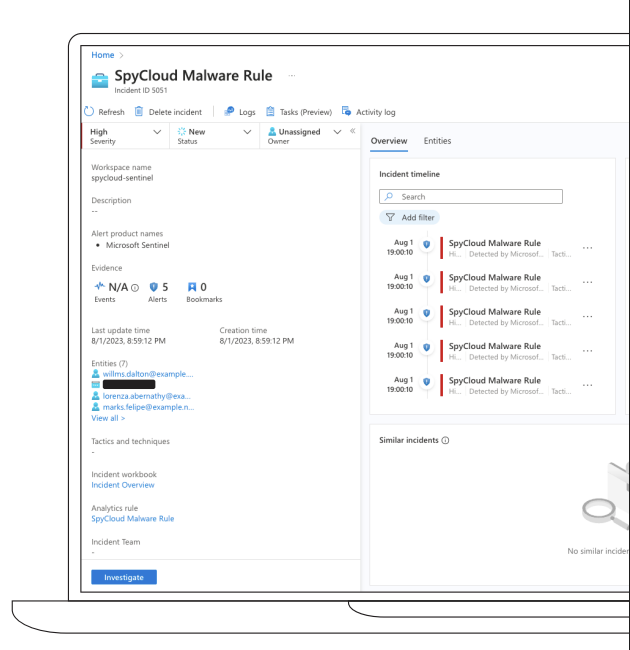
🔎 Investigate & act on real evidence
Spend time on actionable alerts by focusing on the highest-risk signals:
- Plaintext or previously exposed credentials (and reuse/variations)
- Malware-sourced artifacts (cookies, tokens) that enable session hijacking
- Phished accounts requiring immediate reset or re-auth
Use Microsoft Sentinel to:
- 🔍 Query SpyCloud exposures across time windows and identities
- 🧩 Correlate identity evidence with local telemetry (IdP, EDR, VPN, SaaS)
- 📝 Auto-create incidents for new breach/malware/phished records tied to your users
- 🔁 Trigger playbooks to remediate: reset credentials, revoke sessions, disable accounts, notify users/admins
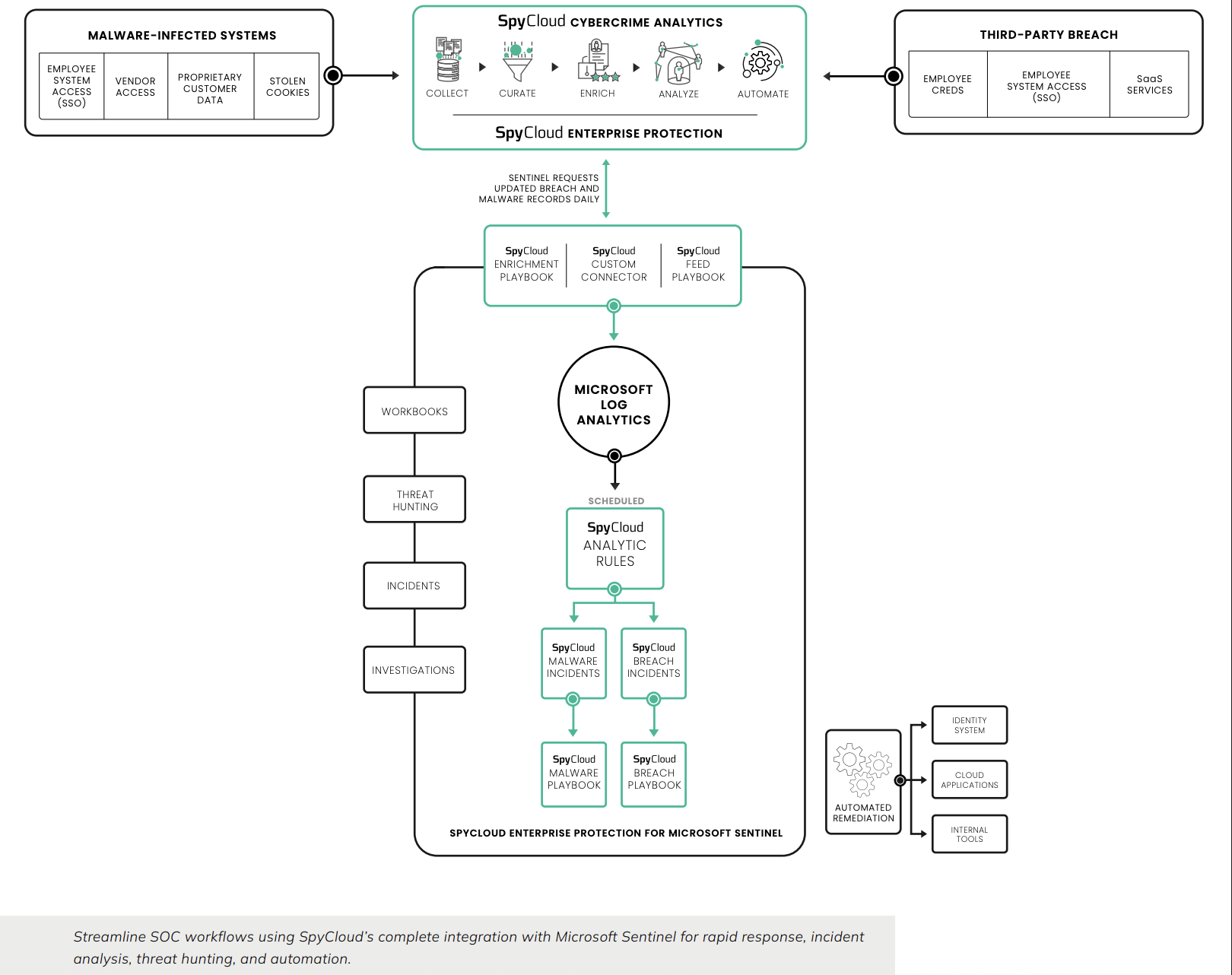
🛠️ How it works (expand)
1) Ingest — bring SpyCloud exposure data into Sentinel
Scheduled ingest of exposure records sourced from breaches, malware infections (infostealer logs), and phished credentials into Microsoft Sentinel.
2) Search & Correlate — make identity signals operational
Run KQL searches to tie SpyCloud identity evidence (credentials, cookies/tokens) to your hosts, SaaS apps, and users; identify high-risk accounts quickly.
3) Detect — analytics rules for high-impact events
Create analytics rules for fresh exposures, plaintext credentials, malware-sourced sessions, and phished accounts. Prioritize by severity and artifact type.
4) Automate — playbooks & response
Use Logic Apps/Playbooks to reset credentials, revoke sessions, force re-auth, disable accounts, and notify end-users/admins from Sentinel incidents.
📊 Dashboards & visuals
- Confirm data ingestion is healthy (counts by source: breach, malware, phished)
- Track exposure trends over time; highlight Critical/High
- Monitor remediation throughput and mean time to response
Tip: Start with a simple “New Exposures by Source & Severity” chart; add “Top Exposed Users” and “Artifacts by Type” (passwords vs. cookies/tokens).
✅ Expected outcomes
- Higher-fidelity detections for identity-based threats from breach / malware / phished datasets
- Faster, automated response via playbooks (resets, revocations, re-auth, disable)
- Reduced exposure window with measurable improvements in MTTR
Updated 29 days ago