Configuring Scan Options
SpyCloud Breach Records
- Select which breach records to scan against: All Records, Last 6 months, Last 3 months, Last month, Last week, Last day
Recommended: All Records (best for detecting password reuse).
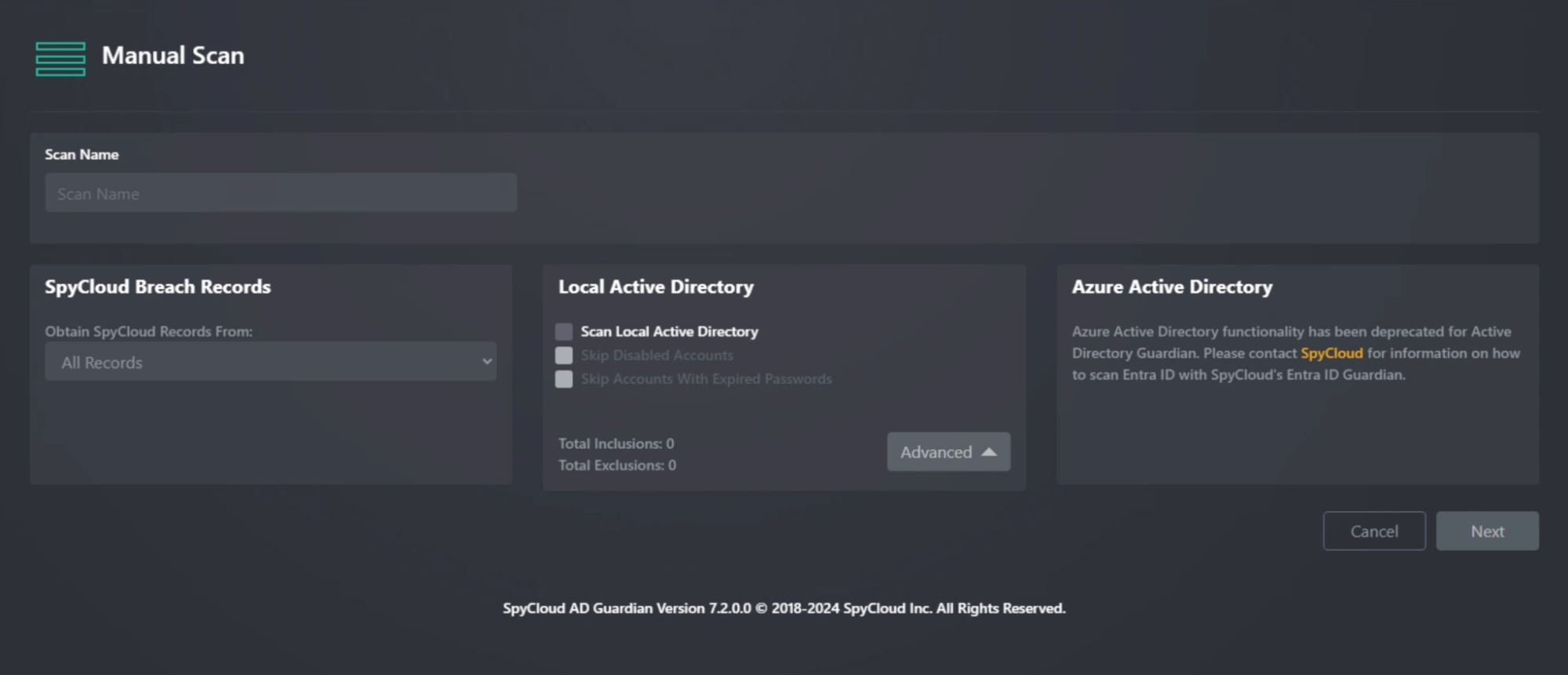
Local Active Directory Scan
Options:
- Scan Local Active Directory
- Skip Disabled Accounts
- Skip Accounts with Expired Passwords (useful for new hires not yet active)
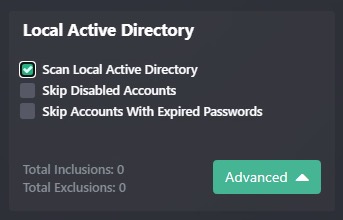
Additionally, you can click Advanced and be presented with options for including and/or excluding collections of users. These collections can be configured under Settings → Collections. For more on this, see Active Directory Object Collection.
Match Type
The next screen of the scan configuration determines what scan types will be performed, along with advanced settings for notifications, reporting, and logging.
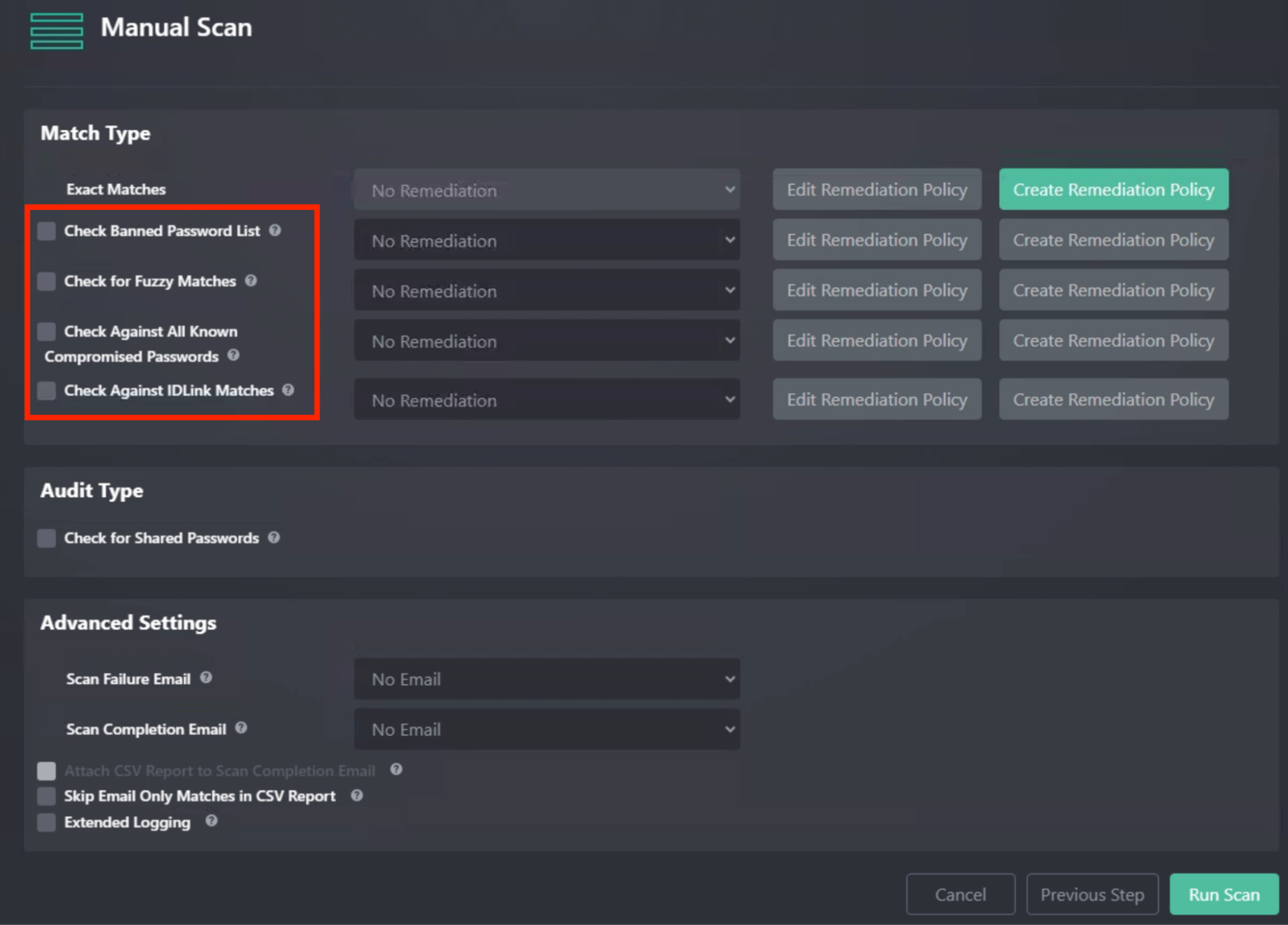
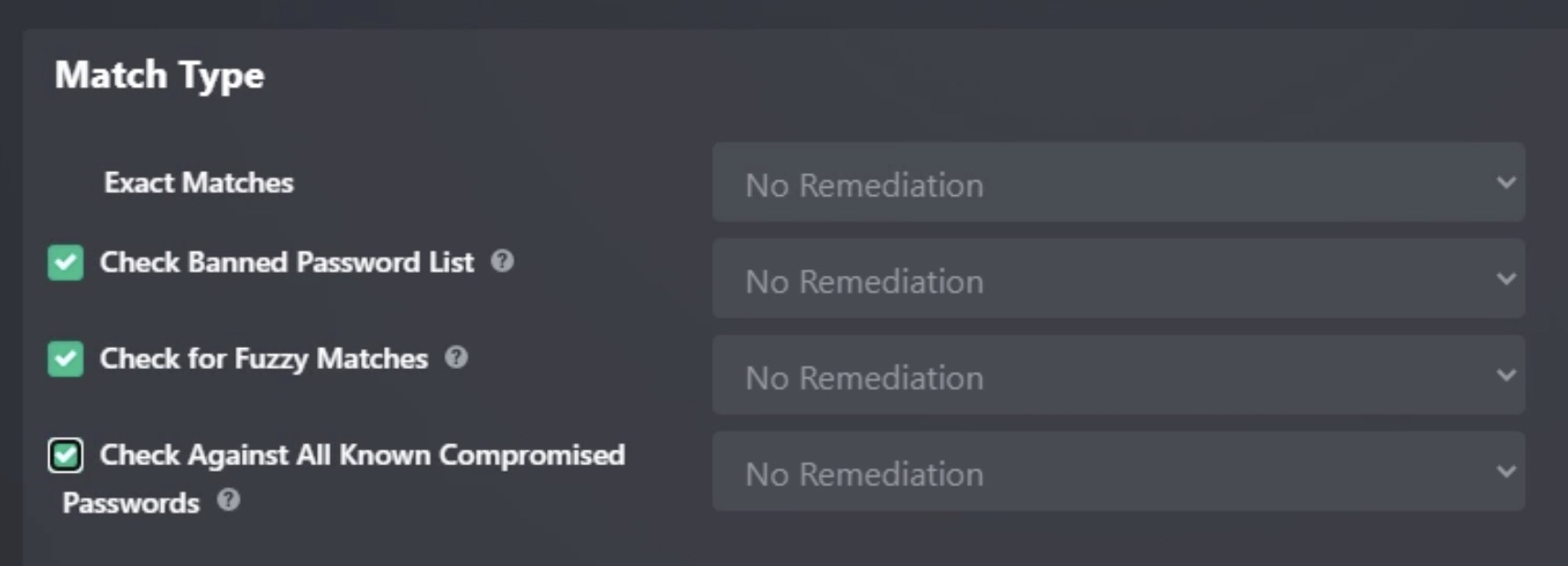
ADG supports multiple match types.
- The Exact Matches scan type is always enabled by default.
- Additional match types can be enabled depending on your organization’s needs.
If multiple match types are selected, ADG will evaluate each account top to bottom.
For example: if an Exact Match is detected, later scan types will not be executed for that account.
🧩 Available Match Types
| Match Type | Description |
|---|---|
| Exact Matches (Always On) | Compares an AD user’s current password against known exposed passwords in SpyCloud breach data. Uses identifiers such as sAMAccountName, UPN, mail, proxyAddresses, and targetAddresses. |
| Check Banned Password List | Compares passwords against a configurable banned list. The default list includes common weak passwords, and admins can add custom entries. |
| Check for Fuzzy Matches | Detects variations of exposed or banned passwords (e.g., slight modifications like Password1! → Password2!). Helps catch near-reuse that may bypass uniqueness policies but remain exploitable. |
| Check Against All Known Compromised Passwords | Compares each user’s AD password against SpyCloud’s entire dataset of known compromised credentials, regardless of associated identity. |
| Check Against IDLink Matches | Uses SpyCloud’s proprietary IDLink identity analytics to detect reuse between work credentials and personal/external exposures tied to the same employee. |
🧠 Why Match Types Matter
Different match types provide varying depth of coverage:
- Exact Matches → Quickest detection of confirmed credential reuse
- Banned Password List → Enforces internal password hygiene policies
- Fuzzy Matches → Finds “creative” but weak variations employees often use
- All Known Compromised Passwords → Ensures no employee password has appeared anywhere in SpyCloud’s recaptured data
- IDLink Matches → Identifies when personal account compromises create corporate risk
🔒 Exact Matches (Always On)
The Exact Matches option is always enabled in ADG.
This scan type checks for matches between a user’s current AD password and any of the exposed passwords found in SpyCloud’s enterprise breach data for that user.
ADG leverages the following account attributes when identifying breach records:
| Attribute | Description |
|---|---|
| sAMAccountName | Windows logon name (legacy username) |
| UPN | User Principal Name (typically email format) |
| Primary email address associated with the user | |
| proxyAddresses | Alternate or secondary email addresses |
| targetAddresses | Targeted or forwarded email addresses |
Because Exact Match runs first, if an exposed password is identified here, other scan types (like fuzzy or banned password checks) will not be attempted for that user account.
🚫 Check Banned Password List
The Check Banned Password List option allows ADG to compare an AD user’s password against a configurable list of banned passwords.
- On a default installation, this list includes common weak passwords.
- Administrators can edit or expand the list to include custom banned passwords.
- The list can be managed in the ADG console by navigating to Banned Passwords in the left-hand navigation.
| Feature | Description |
|---|---|
| Purpose | Detects weak or common passwords in use by AD accounts. |
| Default List | Pre-populated with widely used insecure passwords. |
| Customization | Admins can add their own entries to enforce org-specific policies. |
| Management | Edit/view list under Settings → Banned Passwords. |
Tip: Keep your banned password list updated to reflect both common global weak passwords and your organization’s known risky patterns (e.g., company name + year).
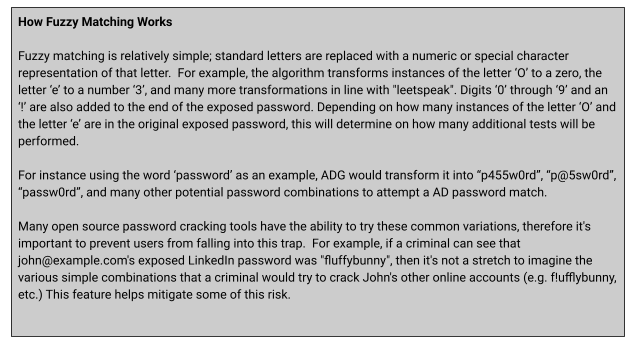
🔎 Check for Fuzzy Matches
The Check for Fuzzy Matches option checks for similarities between a user’s AD password and:
- Variations of their previously exposed passwords
- Variations of banned password list entries (if that option is enabled)
This check helps identify users who reuse the same or very similar password with only slight changes. While these variations may pass uniqueness policy tests, they remain highly exploitable by attackers using common password mutation techniques.
📑 Details
| Feature | Description |
|---|---|
| Purpose | Detects weak password reuse patterns across slight variations. |
| Examples | Password1! → Password2! or Summer2023! → Summer2024! |
| Works With | Variations of both exposed credentials and banned password list entries. |
| Benefit | Flags users who try to “game” uniqueness rules but still use unsafe passwords. |
Fuzzy matching is critical because attackers often run brute-force attempts with simple password mutations, making these accounts more vulnerable if not detected.
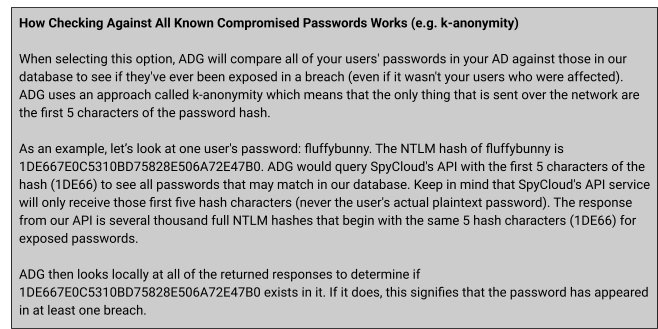
🌍 Check Against All Known Compromised Passwords
The Check Against All Known Compromised Passwords option compares each AD user’s password against SpyCloud’s entire dataset of recaptured credentials.
- Ensures detection of password exposure even if the password has no direct link to that user’s corporate identity.
- Provides the broadest safety net across billions of exposed credentials.
📑 Details
| Feature | Description |
|---|---|
| Scope | SpyCloud’s full corpus of compromised passwords. |
| Purpose | Identifies risky passwords even if they have not been linked to your users specifically. |
| Benefit | Prevents employees from using a password that has ever been exposed, regardless of source or context. |
This is a more resource-intensive scan but provides maximum assurance that no compromised password is in use across your AD environment.
🔗 Check Against IDLink Matches
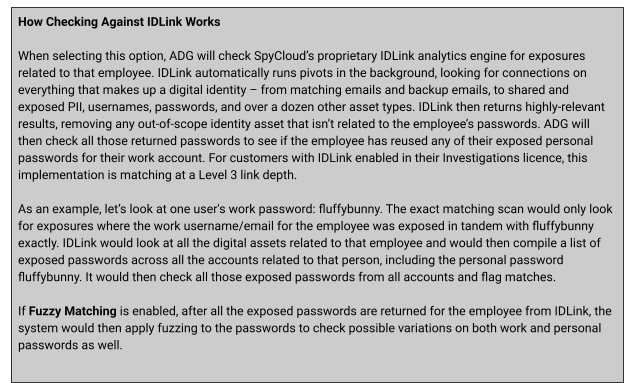
The Check Against IDLink Matches option leverages SpyCloud’s proprietary IDLink™ identity analytics to identify cross-identity password reuse.
- Detects when an AD user’s password matches one exposed in a personal or external account breach.
- Highlights risky behavior where employees reuse personal passwords for corporate accounts.
📑 Details
| Feature | Description |
|---|---|
| Scope | Passwords tied to the employee across personal and corporate exposures. |
| Purpose | Uncovers risk when staff reuse credentials across different accounts or domains. |
| Benefit | Enables remediation even when compromised credentials originated outside of the work environment. |
IDLink helps connect the dots between an employee’s personal and professional identities, making it possible to stop attacks stemming from password reuse across ecosystems.
📝 Audit Type
ADG 7.3 currently supports one audit option during scans: Check for Shared Passwords. More audit options will be available in future releases.
The Check for Shared Passwords option allows ADG to identify Active Directory accounts that are using the same password.
📑 Details
| Feature | Description |
|---|---|
| Purpose | Detects AD accounts that share identical passwords across users. |
| Benefit | Highlights risky practices such as shared service accounts or employees reusing a common password. |
| Use Case | Helps enforce account hygiene and separation of duties by flagging password reuse in your domain. |
Password sharing significantly increases the risk of account takeover, since compromise of one account can expose multiple accounts at once.
🛠️ Remediation Options
Once you’ve determined which scan types to run, you can decide what remediation actions ADG should apply when matches are detected.
- The default option is No Remediation.
- This is recommended for your first scan, so you can review results before enforcing actions.
For configuring remediation policies, you can:
- Select Create Remediation Policy to define new actions
- Or choose Edit Remediation Policy to adjust existing ones
For more details, see [Configuring Remediations].
Options Summary
| Option | Description |
|---|---|
| No Remediation (default) | Runs scans but does not enforce actions. Recommended for initial testing. |
| Create Policy | Define remediation steps to take when matches occur. |
| Edit Policy | Adjust or refine existing remediation policies. |
Tip: Run your first few scans withNo Remediation to validate results, then configure policies for automated remediation once you are confident in your setup.
⚙️ Advanced Scan Settings
To choose the email template used for scan failures, select an email template next to Scan Failure Email. To choose an email template used for scan completion, select an email template next to Scan Completion Email.
There are default templates available to use or you can create and customize your own templates. You will not be able to select emails here unless you have configured your SMTP settings here: [Configuring SMTP].
For information on creating your own email templates, see [Email Templates].
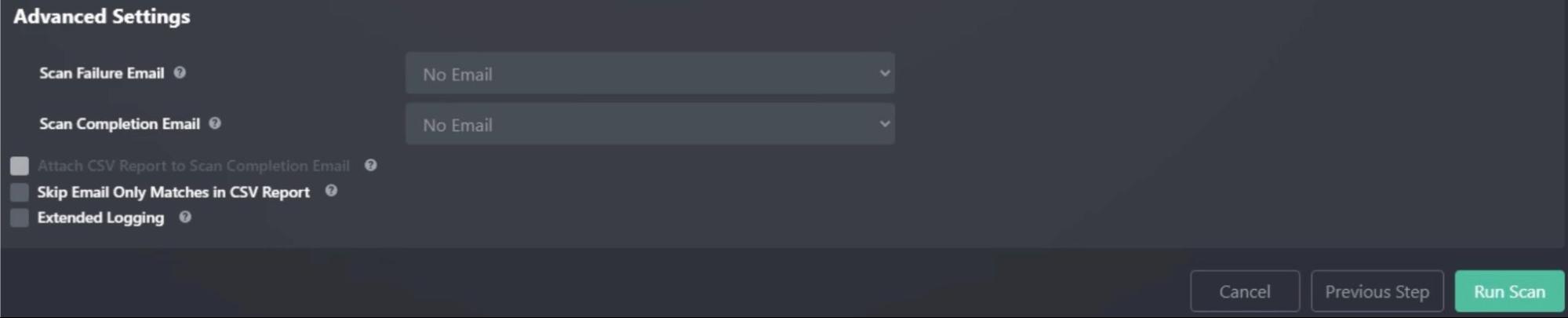
If you choose to configure a Scan Completion Email, you can then also decide if you want a CSV report of the scan and optional shared password report attached to the completion email by checking Attach CSV Report to Scan Completion Email. Additionally, if you’d like the CSV to only contain password matches, select Skip Email Only Matches in CSV Report.
Turning on Extended Logging will cause more details to be written to the debug log file to aid in diagnosing problems. Generally, this should only be used when debugging or if SpyCloud support asks you to do so. (See Debug and Extended Logging for more information).
Once you have finished setting up your scan options, you can run the scan by clicking Run Scan.
Updated 6 months ago