Session Identity Protection
Stop session hijacking and authentication bypass.
SpyCloud Session Identity Protectionidentifies malware-exfiltrated authentication cookies tied to your applications and alerts you so you can invalidate compromised sessions and lock criminals out—even when they try to bypass passwords, passkeys, or MFA.
🚨 The Challenge
Modern infostealer malware is prolific and evasive – often executing and auto-deleting before AV tools detect it. Criminals prize session cookies because they enable session hijacking that bypasses all forms of authentication. As long as the cookie remains valid, an attacker can impersonate a trusted device and walk into the account.
✅ What Session Identity Protection Helps You Do
| Outcome | What it means in practice |
|---|---|
| Stop targeted ATO | Invalidate compromised sessions so stolen cookies become worthless. |
| Prevent authentication bypass | Identify valid cookies criminals could replay to emulate a consumer’s session and bypass security controls. |
| Identify infected consumers | Pinpoint malware-infected users to protect high-value accounts and notify them with guidance. |
⚙️ How It Works
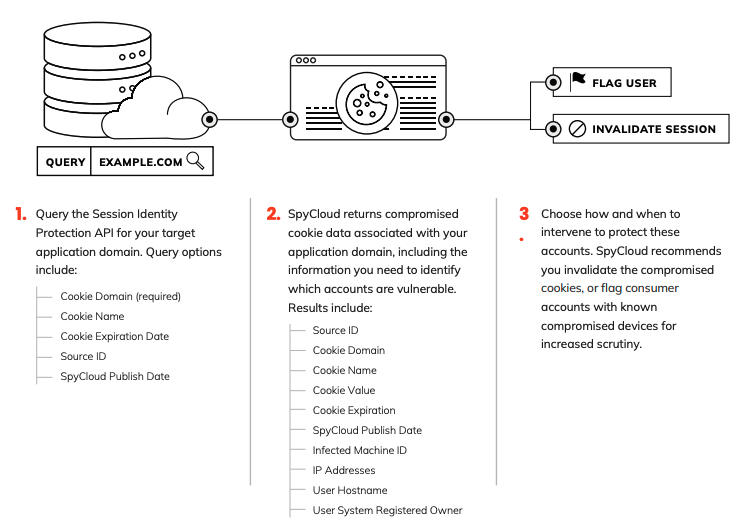
-
Query the API for your target application domain. Query options include:
Cookie Domain (required),Cookie Name,Cookie Expiration Date,Source ID,SpyCloud Publish Date. -
Receive results with the data you need to identify vulnerable accounts, including:
Source ID,Cookie Domain,Cookie Name,Cookie Value,Cookie Expiration,SpyCloud Publish Date,Infected Machine ID,IP Addresses,User Hostname,User System Registered Owner. -
Intervene to protect accounts: invalidate compromised cookies and/or flag accounts tied to known-infected devices for increased scrutiny.
Why this works: SpyCloud continuously recovers malware logs from the criminal underground, parses cookies relevant to your apps, enriches them for identification, and delivers alerts via a high-volume REST API—shrinking the exposure window.
🧭 Recommended Response Patterns
- Immediate session kill: Invalidate any cookie returned by the API that matches your domains.
- Risk-based friction: Step-up auth (MFA, re-verify email/phone) on subsequent high-risk actions from affected accounts.
- Infection follow-up: Notify consumers associated with Infected Machine ID/IP/Hostname to remediate malware.
🧰 Request & Response At-a-Glance
Request filters (combine as needed)
| Filter | Notes |
|---|---|
| Cookie Domain | Required; target your app’s cookie domains. |
| Cookie Name | Narrow to specific auth cookies. |
| Cookie Expiration Date | Focus on still-valid sessions. |
| Source ID / Publish Date | Trace back to specific collections/time windows. |
Response fields (used to locate & protect accounts)
| Field | Use |
|---|---|
| Cookie Domain / Name / Value | Match and invalidate sessions on your side. |
| Cookie Expiration | Prioritize still-active sessions. |
| Infected Machine ID / IP / Hostname / Registered Owner | Correlate to a user profile; trigger outreach or extra scrutiny. |
| Source ID / Publish Date | Audit lineage; analyze campaigns over time. |
🧪 Example Playbook
- Poll or query the API for your cookie domains.
- Join results to customer accounts using cookie metadata & account telemetry.
- Expire sessions matching returned cookies; step-up on next login.
- Case-manage repeat infections using machine identifiers to reduce reinfection risk.
Updated 29 days ago