Palo Alto Cortex XSOAR
For SpyCloud Enterprise Protection.
🤖 Enterprise Protection for Cortex XSOAR
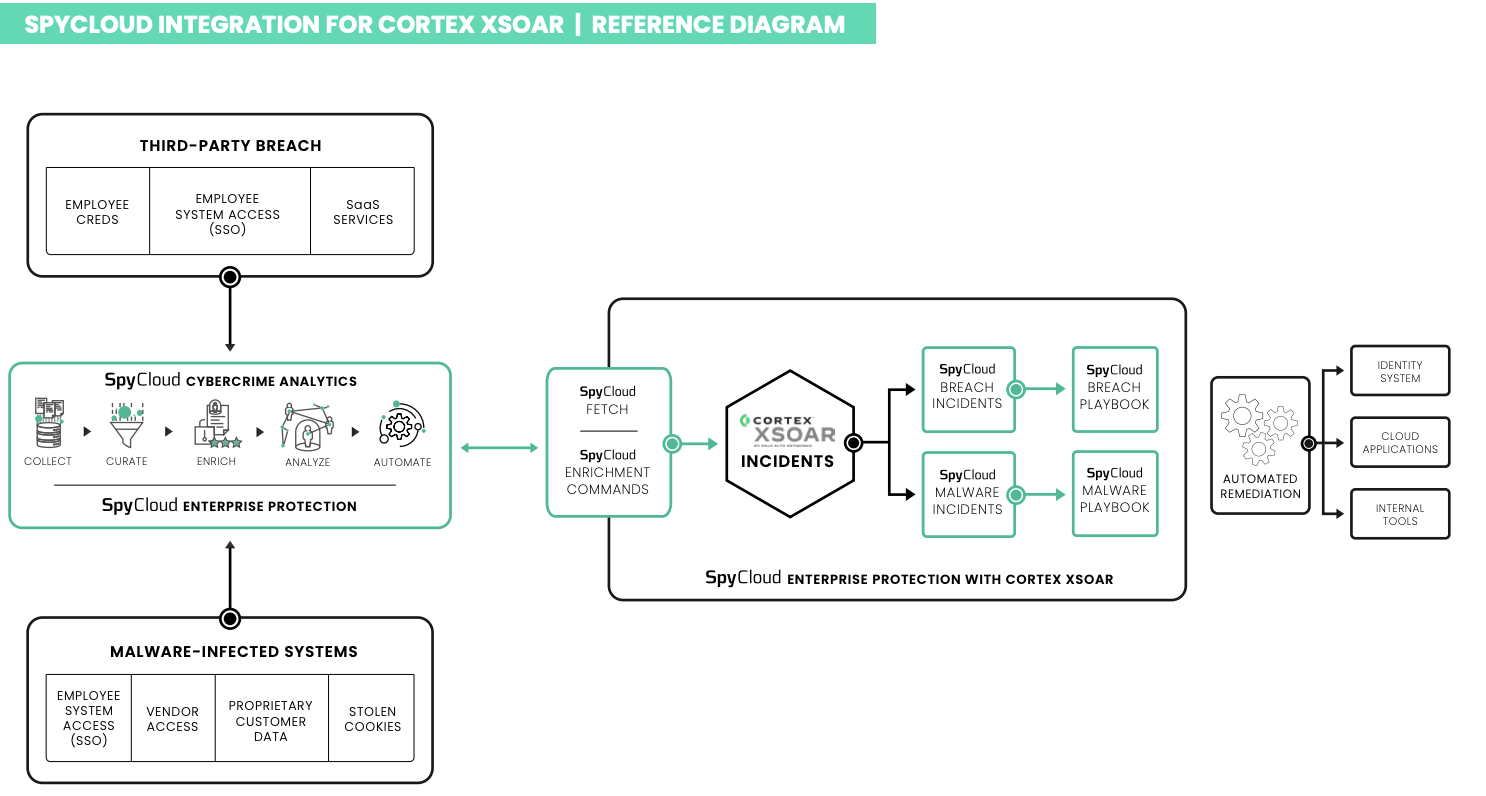
Use SpyCloud’s recaptured darknet exposure data – from breaches, malware-infected devices, and successful phishing – to automate incident response in Cortex XSOAR. Generate and triage incidents, enrich with SpyCloud evidence, and run policy-driven playbooks to reset credentials, revoke sessions, notify users, and more.
Cortex XSOAR Marketplace listing
🚀 What you get (at a glance)
- Ingest & act on identity exposures from breach, malware, and phished sources
- Pre-built playbooks to standardize triage and remediation
- High-priority incidents created automatically for fresh exposure matches
- Enrichment on demand: call SpyCloud APIs directly from XSOAR tasks to pull context
Result: lower MTTR and repeatable response based on reliable identity evidence (plaintext creds, cookies/tokens), not just heuristics.
🧭 Quick start
- Install the SpyCloud Enterprise Protection integration from Cortex Marketplace.
- Configure your SpyCloud API key (with access to breach, malware, and phished datasets).
- Import or clone the starter playbooks and set inputs (severity thresholds, notification channels).
- Test with a sample exposure record to validate incident creation + enrichment.
- Go live and monitor incident volume, response times, and completion rates.
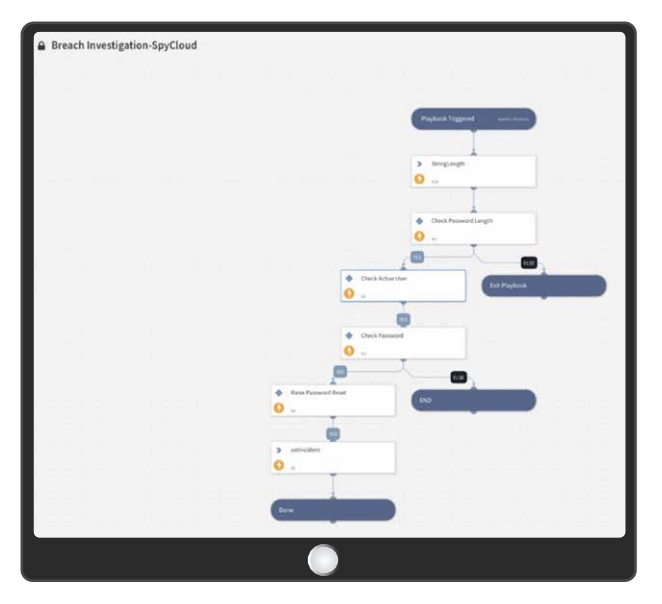
🧱 Playbooks & tasks (customize as needed)
- Source-aware triage — branch logic for breach vs malware vs phished
- Artifact-aware actions — different steps for plaintext credentials vs cookies/tokens
- Remediate — reset credentials, revoke sessions, force re-auth, disable accounts
- Notify & document — Slack/email to users & owners, attach evidence, close with disposition
- Escalate — queue edge cases to a human (e.g., executives, privileged accounts, repeat offenders)
🛠️ How it works (expand)
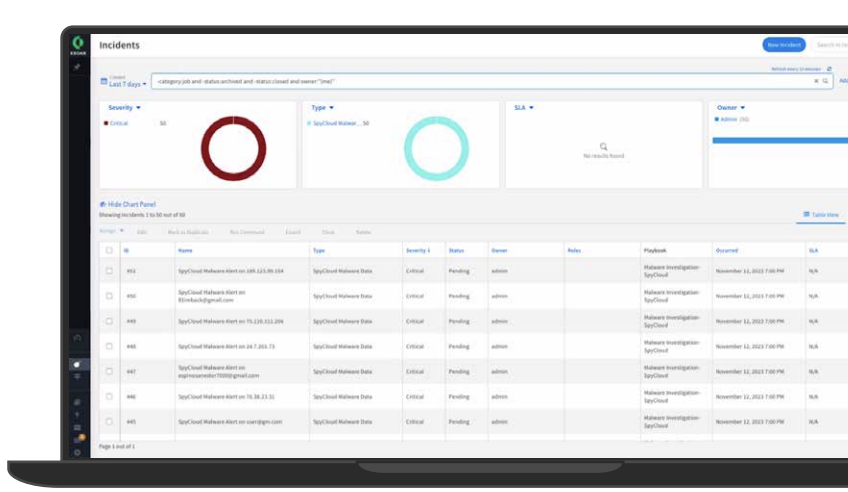
1) Ingest — create incidents from SpyCloud exposure data
Scheduled jobs pull SpyCloud exposure records from breach, malware (infostealer logs), and phished sources. New matches raise incidents with context (user, artifact type, severity, timestamps).
2) Enrich — pull more context via SpyCloud API
Tasks call SpyCloud API to fetch additional evidence (e.g., previous exposures, password reuse indicators, cookie/token presence) and attach it to the incident.
3) Decide — route by source, severity, role
Playbook branches on source (breach/malware/phished), severity (Critical/High), and user role (VIP/admin) to choose the appropriate actions and notifications.
4) Act — automate the fix
Reset passwords, revoke sessions/tokens, enforce re-auth, disable accounts, and notify affected users/owners.
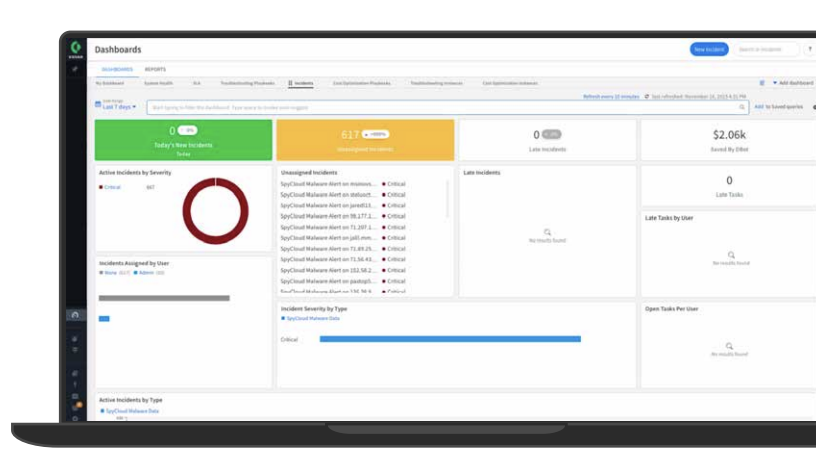
📊 Validation & reporting
- Confirm incident creation for new breach / malware / phished matches
- Track time-to-first-action and overall MTTR
- Monitor automation success (resets, revocations, notifications)
- Trend exposures by source and artifact type (passwords vs cookies/tokens)
Tip: Add a final task to tag incidents with source & artifact type for easy reporting.
Updated 29 days ago