SpyCloud Connect
Hosted automation wtih custom workflows – the data you need, wherever you need it.
🤝 SpyCloud Connect — Hosted Automation
Security teams want automation and trustworthy data. With SpyCloud Connect, you don’t have to choose: we build hosted custom workflows that integrate SpyCloud products with the tools you already use – enabling rapid remediation and scalable automation of compromised identities across your tech stack.
TL;DR: Tell us the workflow and destinations, and we’ll build it, maintain it, and support it for you.
✅ Benefits at a glance
- Custom Workflows – Define your logic for ingesting and remediating identity exposures.
- Development-free – SpyCloud sets up native connectors and builds the workflows for you.
- Zero Maintenance – We maintain & support your workflows so your team can focus on priorities.
- Any Data, Anywhere – Automate in the tools you already use; scale operations confidently.
SpyCloud can integrate with any tool – whether you prefer to send SpyCloud data into your stack directly, or use SpyCloud Connect as a hosted automation service we build, maintain, and support for you.
🔧 How it works
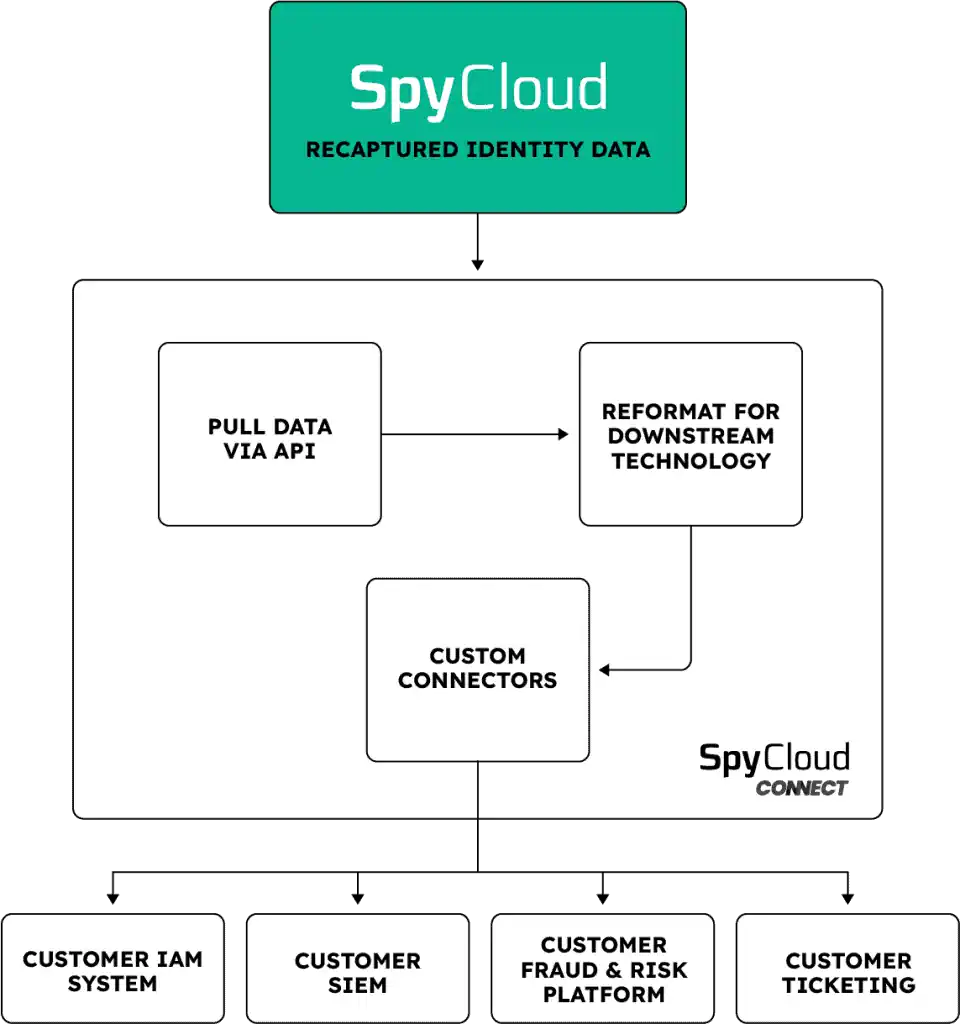
SpyCloud Connect pulls data from SpyCloud Enterprise Protection via API, applies any required transformations, and delivers it to your destinations via custom connectors (e.g., SIEM, ticketing, IAM, EDR/XDR).
1) You choose – desired workflows & destinations
Pick your tools and logic (SIEM, SOAR, TIP, EDR/XDR, IdP/IAM, ticketing, etc.).
2) We build – low-code custom connectors
SpyCloud engineers implement ingestion, transforms, and routing for your use cases.
3) We maintain – zero-maintenance operations
Workflows are supported and kept current as our data lake and ingestion grow in real time.
4) You run – in your tools, on your terms
Operate and measure outcomes in your own stack; we handle the plumbing.
You can integrate any combination of preferred tools (SIEMs, SOARs, TIPs, EDR/XDR, Identity Providers, Ticketing, etc.)
📦 What’s included (the service)
- Build + Support + Maintenance for your custom workflow(s) across teams.
- The base SKU includes one custom workflow with up to three integration destinations.
- Downstream data customization to:
- Enforce least-privilege (limit sensitive fields).
- Add descriptive elements to enrich returns.
- Dynamic updates as SpyCloud’s data lake and ingestion grow — your workflows stay current.
Additional customization / edits
- Need more? We can add specific transforms in our low-code environment.
- If you change vendors later, we’ll swap the destination at no additional cost.
⏱️ Delivery cycle
- SLA: up to 90 days for delivery of a custom automation workflow.
- Typical deployments: 2–4 weeks, often aligned with onboarding.
🧠 Compatible products & data sources
- Built to operationalize SpyCloud’s identity evidence from breaches, malware-infected devices, and successful phishes across your stack.
- Common pairings include Compass (Malware Exposure Remediation) and Employee ATO Prevention.
📚 Customer-favorite workflows

These are examples; Connect will implement your workflow, not force you into ours.
🧭 Getting started
- Define goals, destinations, and policy logic (who/what/when).
- Approve data transformations & least-privilege field sets.
- Implement (SpyCloud builds), UAT, then go live.
- Measure time-to-respond and remediation throughput; iterate.
Contact your CSM to scope a SpyCloud Connect service engagement for your desired workflows.
Updated 29 days ago