Compromised Applications
SpyCloud surfaces exactly which applications were exposed on infected supplier devices
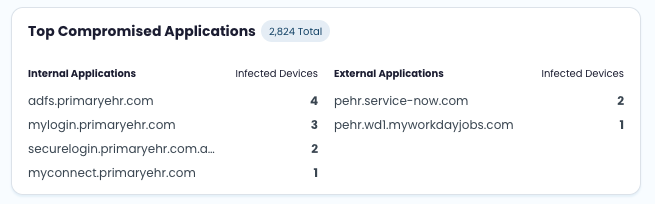
View the Top 10 internal and external applications by infected devices
Understanding Compromised Applications
The Top Compromised Applications view highlights business applications exposed on malware-infected vendor devices. This component helps you understand which applications attackers may already have access to and which exposures present the greatest downstream risk.
Applications are ranked by the number of infected devices, making it easier to prioritize investigation and remediation.
What this shows
Top Compromised Applications summarizes applications observed in malware data that are associated with a company.
Key characteristics:
- Based exclusively on malware records
- Ranked by unique infected devices
- Includes both internal and external applications
- Designed to surface unauthorized access, not configuration weaknesses
How it works
SpyCloud associate records to a company using the record’s domain, which is derived from an email address. Top Compromised Applications adds an important enhancement.
Standard association
- Records are associated when the record’s domain matches one of the company’s monitored domains.
Special case: domainless malware records
- Some malware records do not contain a domain.
- Supply Chain Threat Protection can still associate these records indirectly if:
- The domainless malware record shares an
infected_machine_idwith another record with a domain that belongs to the company
- The domainless malware record shares an
This allows SpyCloud to capture application exposure that would otherwise be missed.
This is especially important for malware data, where application URLs are often captured without a clear company domain.
Understanding the view
The Top Compromised Applications component includes several key metrics to help interpret exposure.
Summary fields
| Field | Definition |
|---|---|
| Total | Total number of records associated with the company’s domain or subdomain. Includes malware records directly associated with the company and those indirectly associated via infected_machine_id. |
Internal applications
Internal applications are applications owned or operated by the company.
How they are identified:
- The application’s subdomain + registrable domain match the company’s domains
Example:
console.spycloud.comis an internal application forspycloud.com
What is shown:
- Top 10 internal applications
- Sorted by number of infected devices
External applications
External applications are third-party applications used by the company’s workforce.
How they are identified:
- The application’s subdomain matches the second-level domain of one of the company’s domains
Example:
spycloud.example.comis external forspycloud.com
What is shown:
- Top 10 external applications
- Sorted by number of infected devices
Application entries
Each listed application includes:
| Field | Definition |
|---|---|
| Target URL | The application URL captured by malware on infected devices. |
| Infected Devices | Total number of unique infected_machine_id values associated with that application. |
How to use this data
- Prioritize investigations on applications with the highest infected-device counts
- Assess business impact by identifying apps tied to sensitive data or privileged access
- Engage vendors with concrete evidence of exposed applications
- Track changes over time to validate remediation and reduced exposure
Updated about 1 month ago